
Thick client applications continue to play a critical role in enterprise environments, especially within banking, finance, ERP systems, trading platforms, HR systems, OT environments, and internal administrative tools. Despite this, thick client security testing is often poorly understood or completely omitted from traditional VAPT engagements. Unlike web applications, thick clients execute significant logic locally and often rely on implicit trust in the endpoint which is a dangerous assumption in today’s threat landscape.
Thick Client vs Thin Client
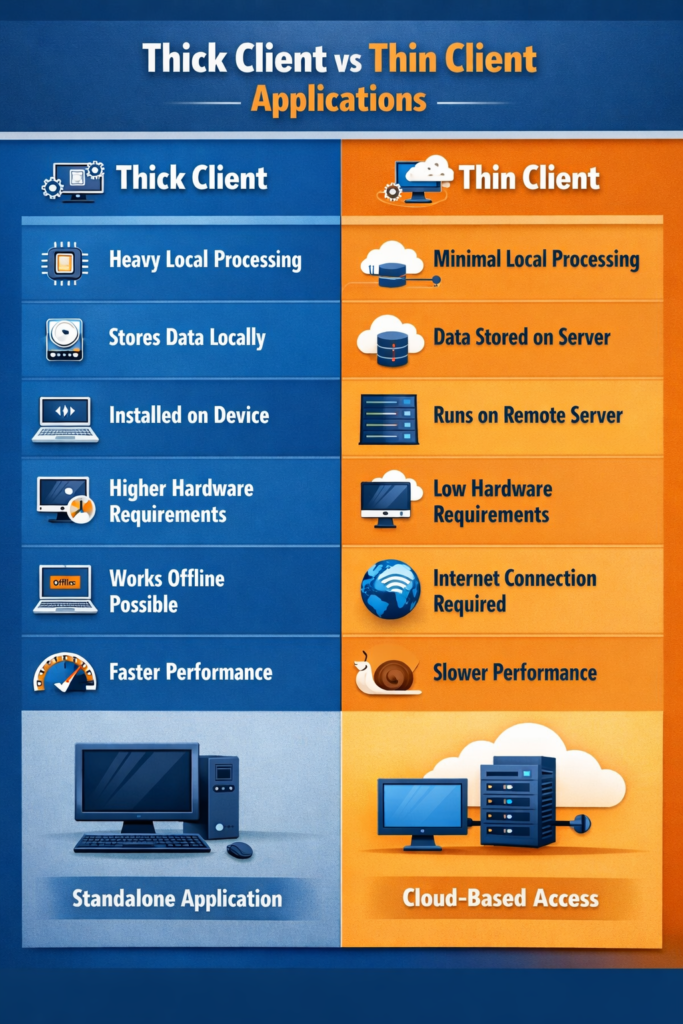
A Thick Client application is an application that performs most of its tasks and stores data locally. It only connects to the server for tasks like syncing a database or sending/receiving files. Thick Client applications primarily:
- Executes business logic locally
- Communicates with backend services
- Often stores configuration and sensitive data locally
Examples of Thick Client applications are Java / .NET desktop applications, Electron apps, Legacy Windows applications etc.
A Thin Client application is an application in which the business logic and stored data lies on the server side. Thin client primarily relies on the backend server for:
- Business logic
- Authorization
- Data processing
Examples of Thin Client applications are Web applications, Browser-based dashboards, SaaS portals etc.
Thick Client Attack Surface
1. Local System Attack Surface
- Executable binaries
- DLLs / JARs
- Configuration files
- Registry keys
- Logs and temp files
- Embedded databases (SQLite)
2. Network Communication
- APIs (HTTP/S, SOAP, gRPC)
- Custom protocols
- Authentication tokens
- Session identifiers
3. Backend Services
- Databases
- File servers
- Message brokers
- Admin APIs
Common Vulnerabilities in Thick Client Applications
1. Hardcoded Credentials & Secrets
- Database credentials
- API keys
- Encryption keys
- Application credentials
- Cloud Access Key/Secret Key
2. Insecure Local Storage
- Plaintext credentials in config files
- Weak encryption
- Predictable file paths
3. Client-Side Authentication & Authorization
- Role validation in client logic
- Feature toggles controlled locally
- Hidden admin functions
4. Insecure Communication
- Unencrypted Communication (No SSL/TLS)
- Weak certificate validation
- Missing certificate pinning
- Replayable tokens
- SSL/TLS Misconfigurations
5. Injection Vulnerabilities
- SQL Injection
- Command Injection
- Insecure deserialization
6. Business Logic Flaws
- Skipping workflow steps
- Price or role manipulation
- Direct object access
7. Excessive Backend Trust
Thick Client Testing Methodology
Phase 1: Reconnaissance & Application Understanding
- Identify technology stack
- Observe workflows
- Locate files and configs
- Monitor runtime behavior
Phase 2: Static Analysis
- Decompile binaries
- Review source logic
- Identify secrets, endpoints, and logic flaws
Phase 3: Dynamic Analysis
- Intercept traffic
- Modify requests/responses
- Bypass client-side checks
Phase 4: Authorization & Logic Testing
- Role escalation
- Feature abuse
- Backend validation checks
Phase 5: Exploitation
- Data exposure Check
- Privilege escalation
- Database compromise
Thick client applications represent a high-risk but under-tested attack surface. Their reliance on client-side trust makes them especially vulnerable in assumed-breach scenarios. Effective thick client testing requires Understanding the client logic, Challenging trust assumptions and Treating the endpoint as hostile.
Leave a Reply