In reconnaissance, what you fail to enumerate is often what hurts the most.
Subdomain enumeration is one of the most critical phases of reconnaissance in any Red Team Assessment. Missed subdomains often mean missed attack surfaces, such as forgotten admin panels, staging environments, internal APIs, or legacy services that were never meant to be exposed publicly. In real-world red-team engagements, subdomain enumeration is not about running a single tool and moving on. It is a multi-source intelligence-gathering process that combines automated tooling, recon frameworks, public data sources, and OSINT techniques to build the most complete asset inventory possible. This guide walks through practical and commonly used approaches for subdomain enumeration, explains when and why each approach is useful, and highlights how professionals combine them for maximum coverage.
Approach-1 : Tool-Based Subdomain Enumeration
Automated tools form the foundation of most enumeration workflows. These tools aggregate data from multiple sources such as certificate transparency logs, passive DNS, search engines, and public datasets.
Commonly Used Tools:
Note: There are more tools apart from the listed 4 tools/scripts, however they are the most known and trusted tools based on obtained results. Other tools can also be experimented to find better efficiency and results.
- Subfinder
- Sublist3r
- Assetfinder
- Amass (passive mode)
Technical Advantages:
- Fast and repeatable
- Passive enumeration (low noise)
- Suitable for large scopes
- Easy to automate and integrate
Technical Constraints:
- Heavily dependent on public data sources
- Overlap between tools is common
- May miss niche or newly created subdomains
Tip: Running one tool is not sufficient. Running multiple tools and deduplicating results significantly improves coverage, as each tool relies on different data sources.
Practical Comparison:
For demonstration purpose we will be using “tesla.com” as their public bug bounty program has this domain listed in their scope and we are authorized to perform any type of testing on “tesla.com”. The below results are just a demonstration to show how results vary with different tools.
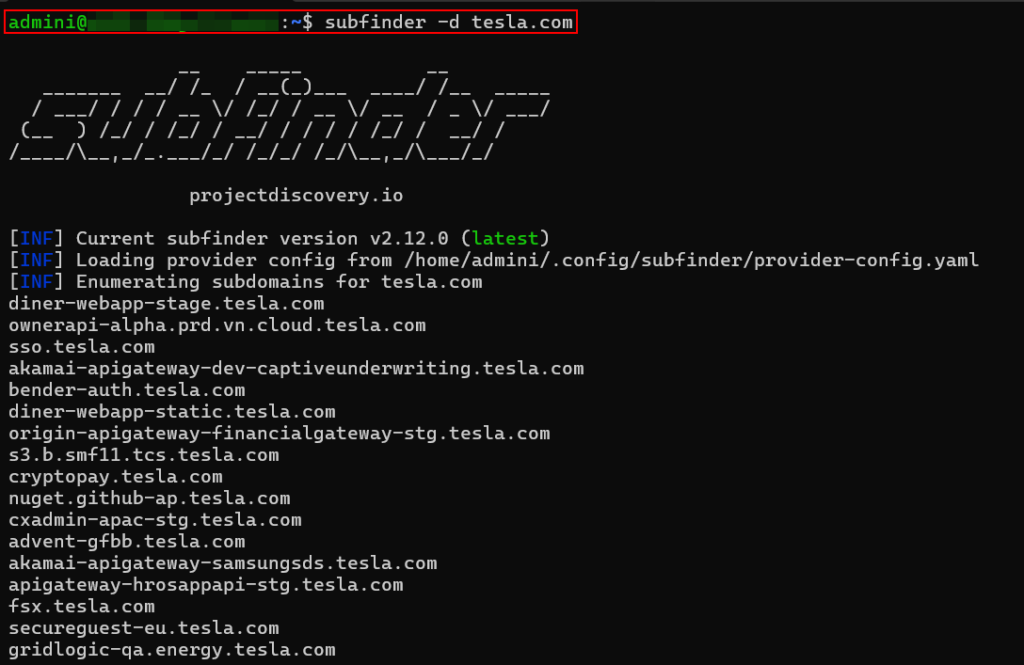
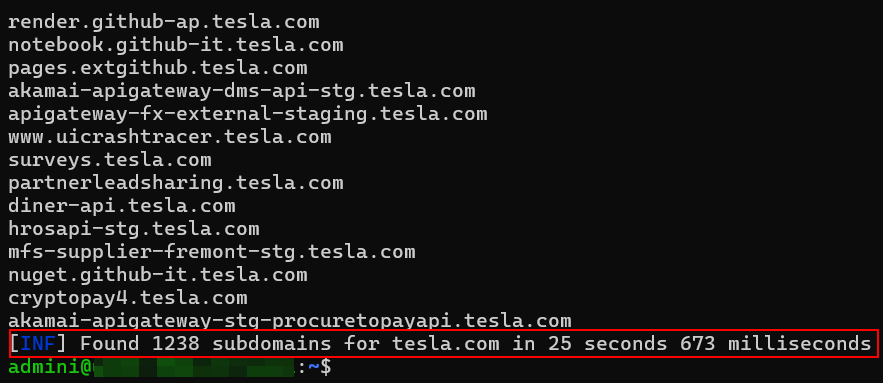
Subfinder:
Enumerated – 1238 Subdomains
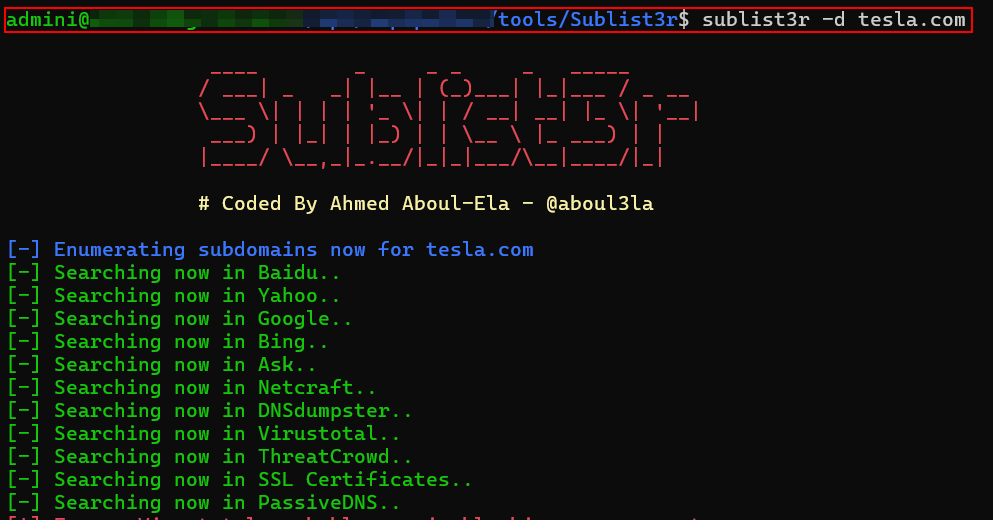
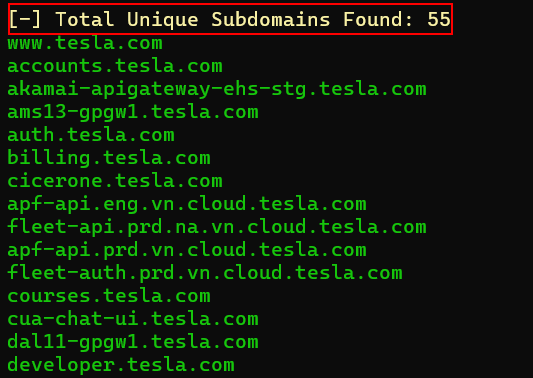
Sublist3r:
Enumerated – 55 Subdomains (Without API Keys)
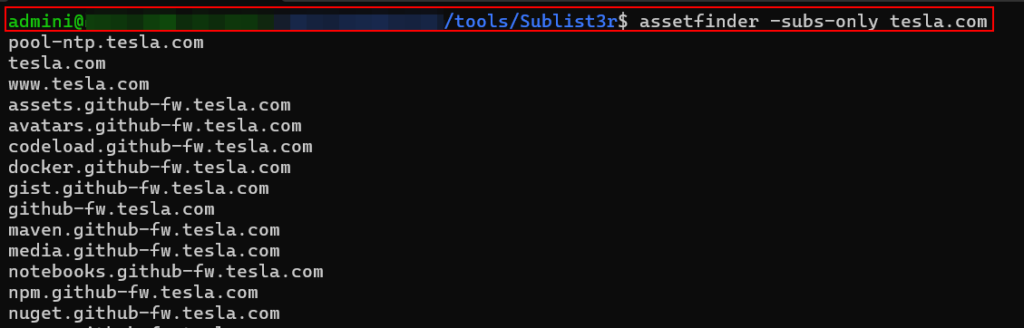
Assetfinder:
Enumerated – 804 Subdomains
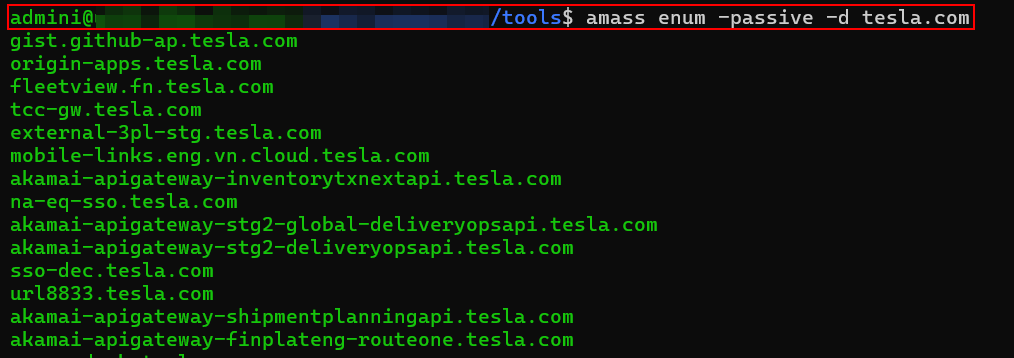
Amass:
Enumerated – 2811 Subdomains (Passive Scanning)
Kindly note passive scanning results have been shown for demonstration, however active scanning can also be performed for better output.
Approach-2 : Recon Frameworks (Focused Recon, Not Full Scans)
Recon frameworks orchestrate multiple reconnaissance steps and tools under a single workflow. While many frameworks support full attack chains, they are most effective when used only for reconnaissance during early-stage assessments.
Popular Recon Frameworks:
- BBOT
- ReconFTW
- reNgine
- Sn1per (recon mode)
- recon-ng
- Spiderfoot
Technical Advantages:
- Suitable for large scopes
- Automates usage of multiple tools, removes duplicates and provides final list
Technical Constraints:
- Lack of customization, heavily reliant on tools mentioned in the framework code.
- Slower as it uses multiple tools
- Might run active scans also in order to enumerate subdomains
- May miss niche or newly created subdomains
Practical Demonstration:
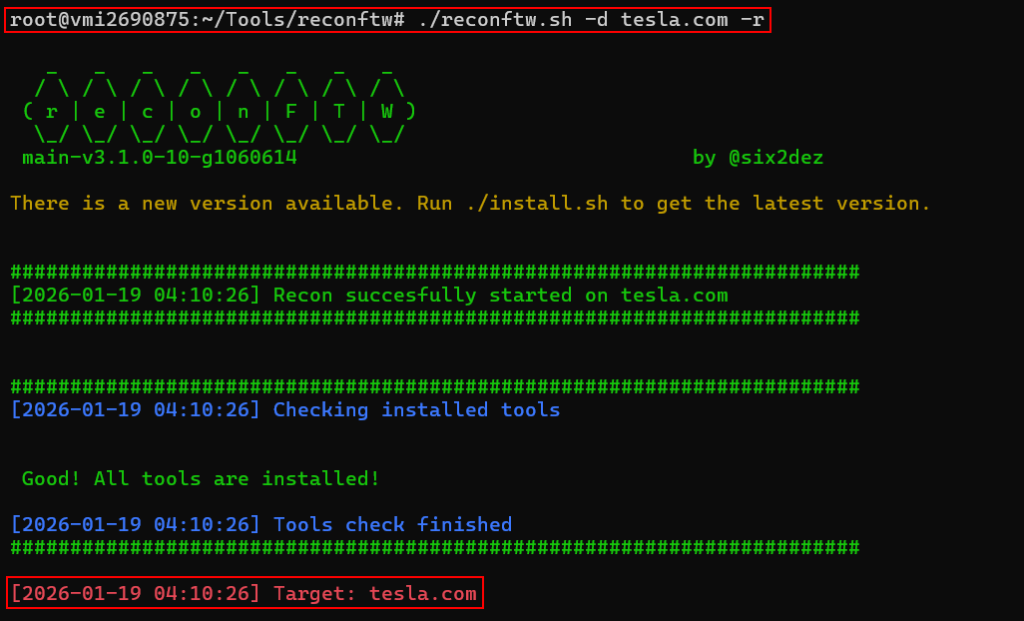
ReconFTW:
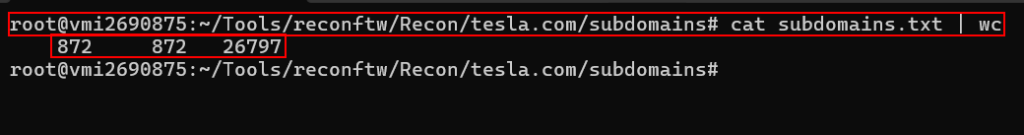
Frameworks like reconftw does not have a single subdomain enumeration method. It is a wrapper/orchestrator that runs multiple passive + active techniques in parallel, then removes duplicates and validates the results. Each framework has their own wordlists, tools and methods to perform subdomain enumeration and recon.
Enumerated – 872 Subdomains
Approach-3 : Public Websites & Search Platforms
Publicly accessible platforms often expose subdomain data that automated tools alone may miss. These platforms index DNS records, certificates, services, and banners at internet scale.
Key Platforms:
- crt.sh (Certificate Transparency logs)
- VirusTotal
- Censys
- Shodan
- FOFA
- subdomainfinder.c99.nl
- ip.thc.org
- Securitytrails
- Zoomeye
- dnsdumpster
Technical Advantages:
- Direct sources from which various tools source the subdomains list
- No installation of tools are required
- Passive enumeration (No noise)
- Very Fast
- Easy to automate using API Keys or API endpoints
Technical Constraints::
- Overlap between tools is common
- May miss niche or newly created subdomains
Practical Comparison:
For demonstration purpose we will just be showcasing 4 web portals through which enumeration is possible.
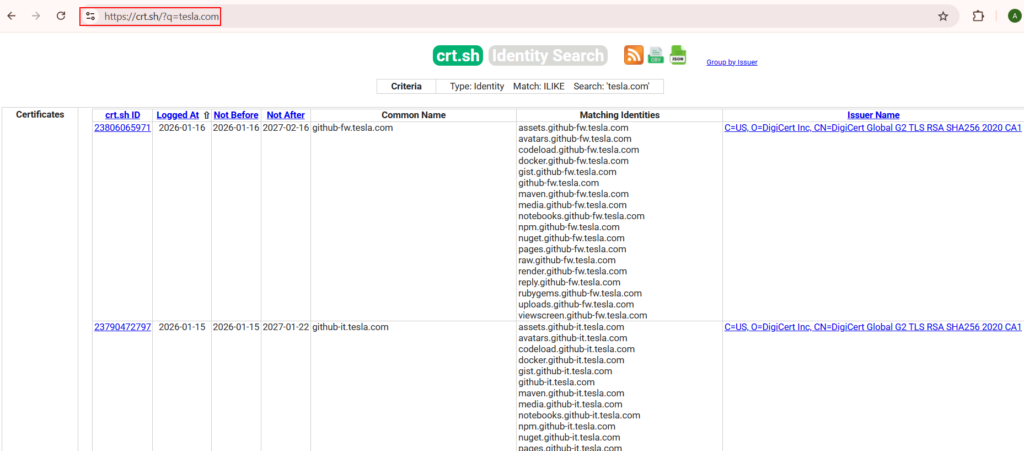
crt.sh (Certificate Transparency Logs):
Enumerated – 461 Subdomains
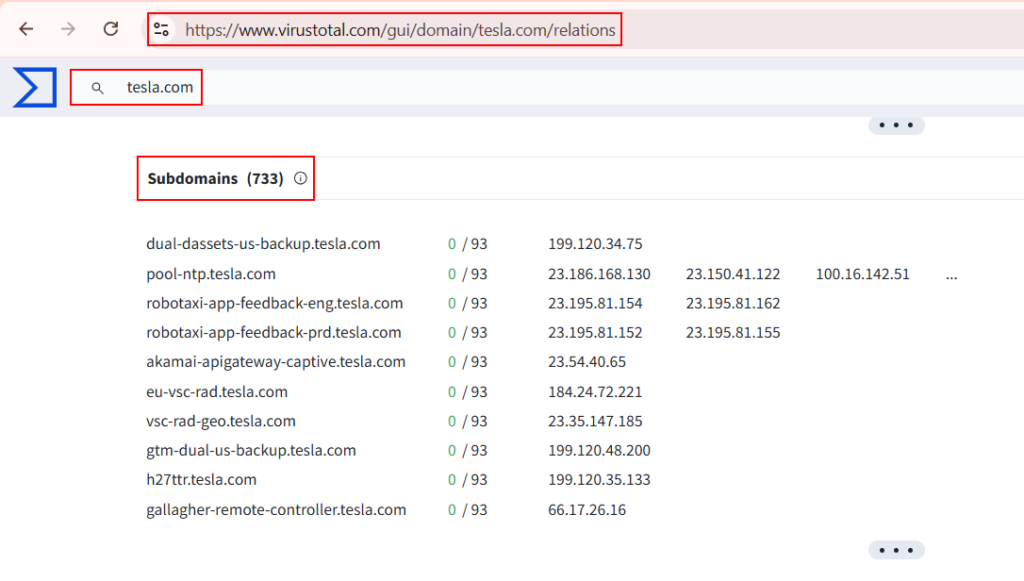
Virustotal:
Enumerated – 733 Subdomains
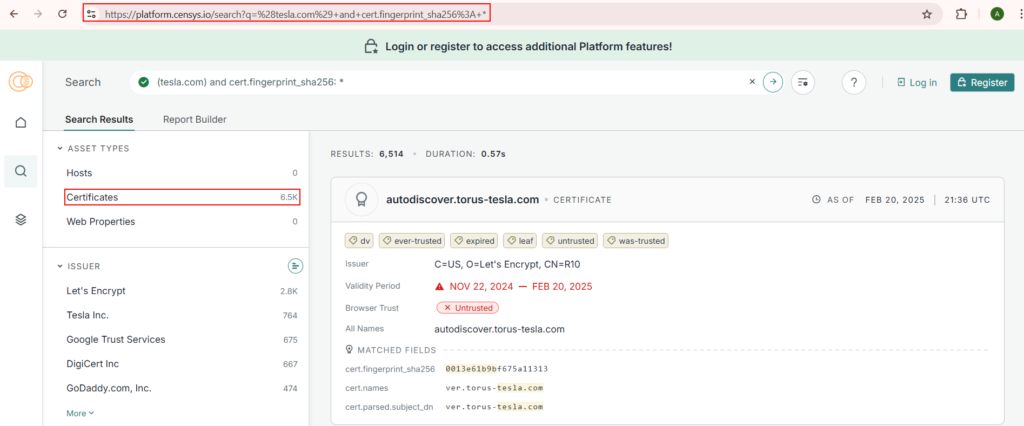
Censys:
As per the dashboard there are more than 6.5K+ certificates, however they can be duplicate entries. The same data can also be obtained using censys cli to automate and remove duplicates.
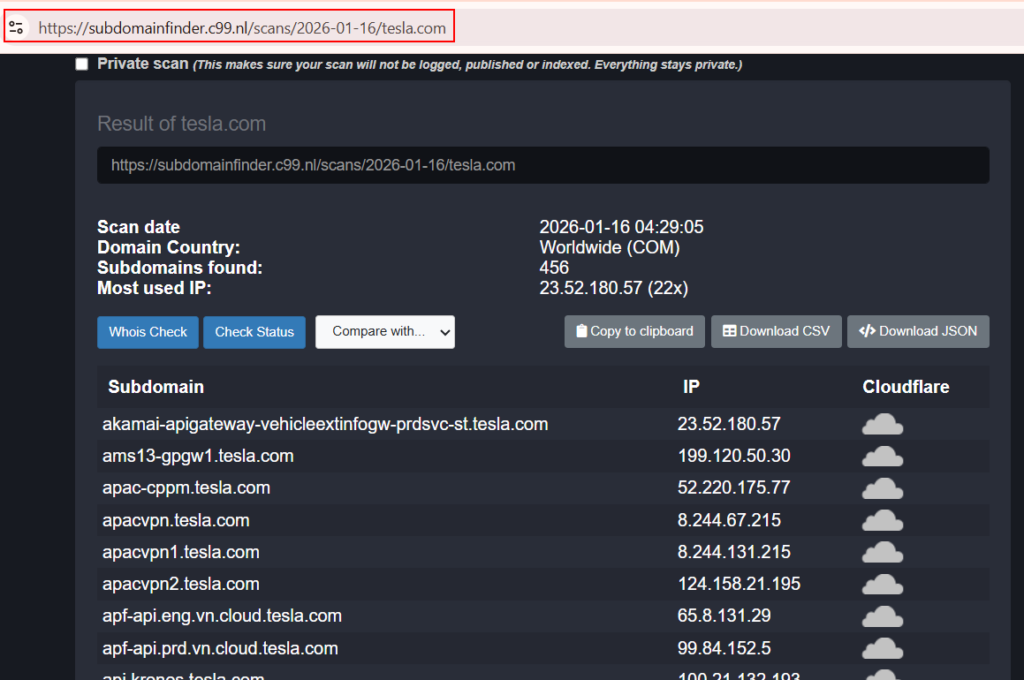
subdomainfinder.c99.nl:
Enumerated – 139 Subdomains
Approach-4 : OSINT-Driven Subdomain Discovery
OSINT techniques go beyond automated tools and leverage human-driven intelligence gathering. These techniques are slower but often yield high-value findings.
Common OSINT Techniques:
- Google Dorking
- GitHub Dorking
- Google Groups
- Paste Sites & Public Forums
- Exposed API Collections (SwaggerHub and Postman)
- API Documentation Pages
Practical Demonstration:
For demonstration purpose we will just be taking 2 techniques into consideration.
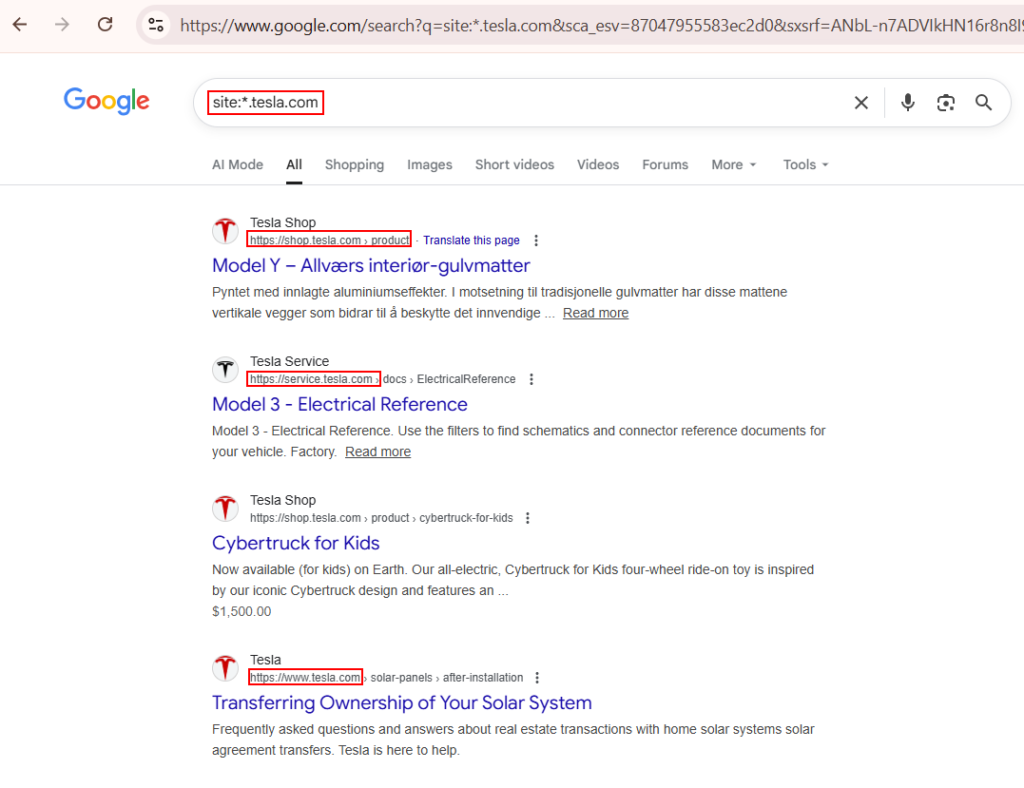
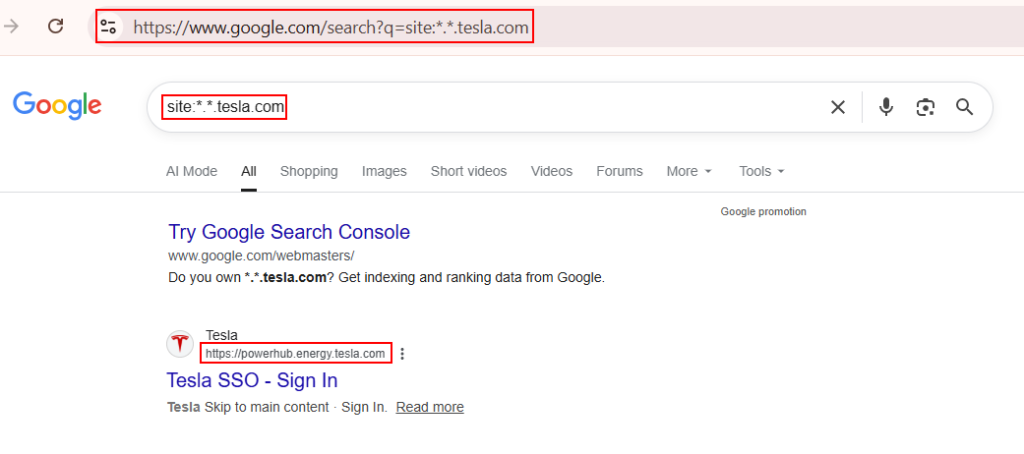
Google Dorking:
Single and Multi Level Subdomains can be obtained using simple dorks such as site:*.tesla.com & site:*.*.tesla.com
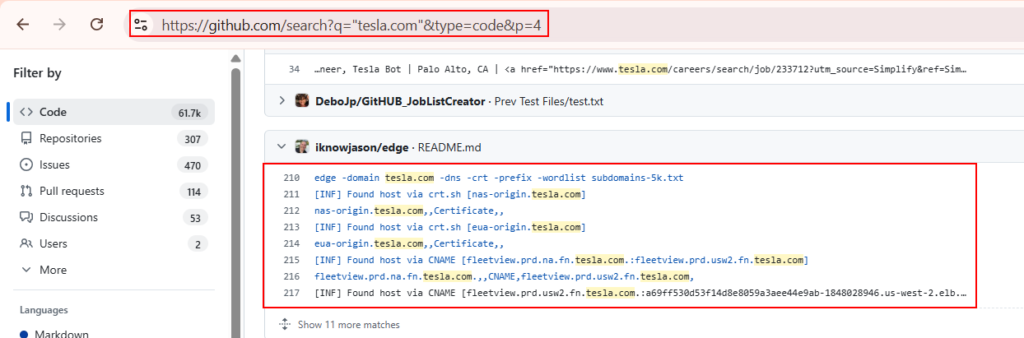
Github Dorking:
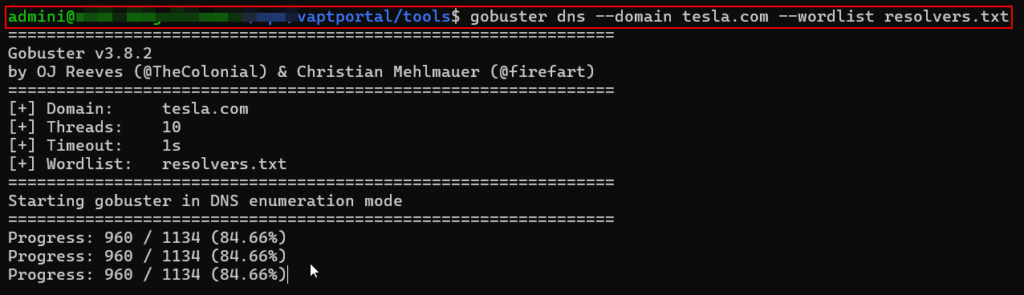
Approach-5 : DNS Bruteforcing (Controlled & Context-Aware)
DNS bruteforcing attempts to discover subdomains by guessing names based on wordlists or known naming conventions.
Commonly Used Tools:
DNS brute-forcing involves actively querying DNS servers using wordlists to identify valid subdomains. As it generates traffic, it should only be used where scope explicitly permits active enumeration. Custom wordlist can be made or wordlist from popular repo like Seclists can be used to perform DNS bruteforcing inorder to identify valid subdomains.
- dnsx
- massdns
- puredns
- amass (Active Mode)
- shuffledns
- knockpy
- gobuster (DNS Mode)
Technical Advantages:
- Custom Wordlist Specific to Organization or Geography as Organization follows predictable naming patterns.
- Internal naming conventions are partially known, bruteforcing might give results that are not indexed publicly.
Technical Constraints:
- Can introduce noise and detection risk
- Less effective without contextual wordlists
Tip: In professional assessments, DNS bruteforcing is most effective after passive enumeration.
Practical Demonstration:
Approach-6 : JavaScript-Based Subdomain Discovery
JavaScript analysis has become one of the most effective modern techniques for uncovering hidden subdomains.
Technical Advantages:
- Internal endpoints and domains are often hardcoded.
- Third-party integrations are frequently exposed.
- May expose subdomains that are of lower environment or not indexed publicly.
Technical Constraints:
- Time consuming task to go through javascript files from various subdomains in order to identify new subdomains.
Practical Demonstration:
It is a manual process which can be automated to certain extent by enumerating js files and creating custom script to scrape all the subdomains from the js files. We can also make use of burp extensions like JS Miner to extract subdomains from JS files as demonstrated below.
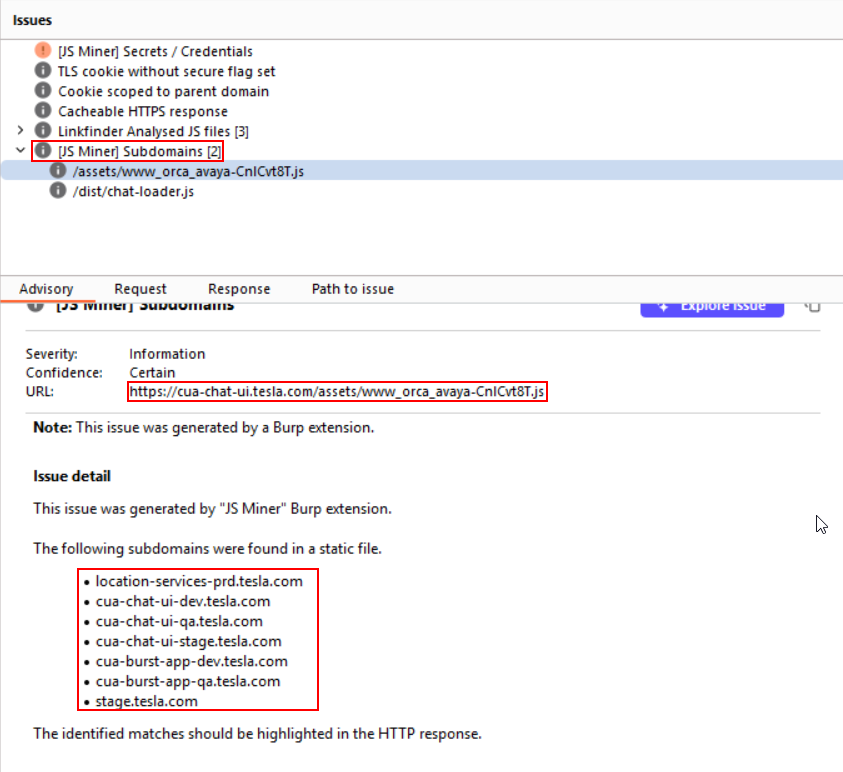
Approach-7 : Web Archives Based Subdomain Discovery
Web archives store historical snapshots of websites and URLs over time. While they are commonly used for endpoint discovery, they are also an effective indirect source for subdomain enumeration, especially for legacy and decommissioned assets.
Commonly Used Web Archive Sources & Tools:
- Wayback Machine
- Common Crawl
- Tools such as gau and waybackurls
Technical Advantages:
- Excellent for discovering legacy and forgotten subdomains
- Passive and low-noise
- Provides historical context about asset evolution
- Useful for long-lived organizations with frequent infrastructure changes
Technical Constraints:
- Results may include non-existent or decommissioned subdomains
- Requires additional verification to determine if assets are still live
- Not effective for newly created subdomains
Practical Demonstration:
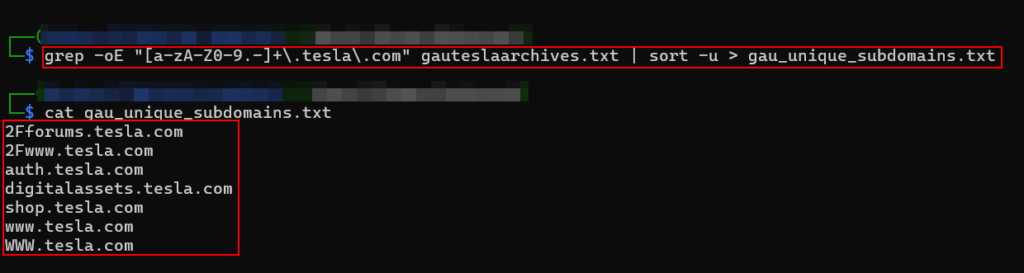
Gau:
Gau can be used with its “–subs-only” flag to save the output inside a text file. The below mentioned command can then be used to filter unique subdomains from the saved archives:grep -oE "[a-zA-Z0-9.-]+.domain.com" gauteslaarchives.txt | sort -u > gau_unique_subdomains.txt
Approach-8 : Response Header Based Subdomain Discovery
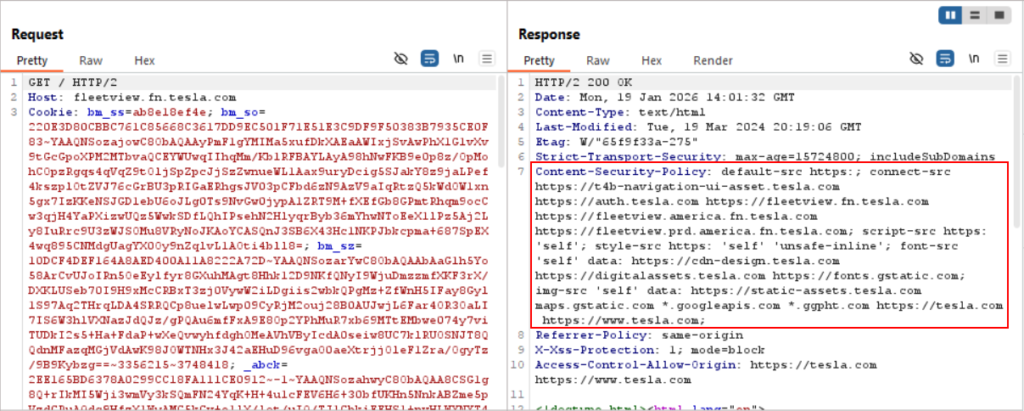
Modern web applications heavily rely on security and headers to define trust boundaries. While these headers are designed to improve security, they often explicitly whitelist domains and subdomains, unintentionally revealing valuable reconnaissance information.
Technical Advantages:
- Internal endpoints and domains are often hardcoded.
- Third-party integrations are frequently exposed.
- May expose subdomains that are of lower environment or not indexed publicly.
Technical Constraints:
- Time consuming task to go through javascript files from various subdomains in order to identify new subdomains.
Practical Demonstration:
Among many headers, Content Security Policy (CSP), Access Control Allow Origin headers are one of the most powerful passive sources for subdomain discovery. Screenshots of some headers giving details about other domains/subdomains belonging to tesla can be seen below.
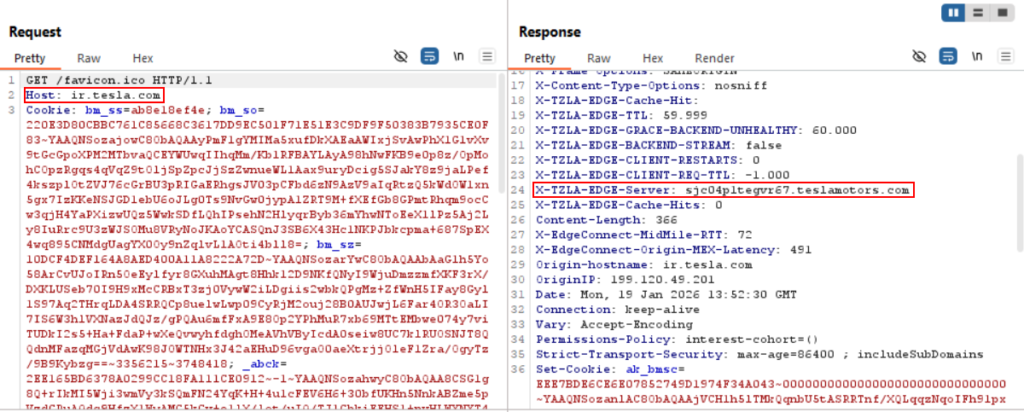
Approach-9 : CDN Based Subdomain Enumeration
Many organizations place their applications behind CDNs such as Cloudflare, Akamai, Fastly, CloudFront, Imperva, Azure Front Door, etc. While CDNs improve performance and security, misconfigurations and CDN metadata often leak additional subdomains that are not easily discoverable through traditional DNS bruteforce. Subdomain enumeration via CDN focuses on identifying origin domains, backend hostnames, staging environments, and alternate service endpoints exposed through CDN configurations.
Example 1: TLS Certificate (SAN / CN) Enumeration via CDN
Command:echo | openssl s_client -connect tesla.com:443 -servername tesla.com 2>/dev/null | openssl x509 -noout -text | grep -A1 "Subject Alternative Name"
Ouput:DNS:tesla.com
DNS:www.tesla.com
DNS:api.tesla.com
DNS:static.tesla.com
DNS:assets.tesla.com
Example 2: CDN Response Header Leakage
Some CDNs and misconfigured origins leak backend or alternate hostnames/subdomains in HTTP response headers.Headers to Inspect: Server, Via, X-Cache, CF-RAY, X-Amz-Cf-Id etc
Technical Advantages:
- Passive in nature
- High accuracy
Technical Constraints:
- Time Consuming
Approach-10 : Namespace Based Subdomain Enumeration
Large organizations commonly rely on namespaces to manage scale, performance, and availability. While these abstractions simplify infrastructure management, they often introduce predictable subdomain patterns that can be leveraged during reconnaissance. This technique focuses on identifying subdomains through service namespaces rather than traditional DNS enumeration alone.
Common Namespace Patterns:
Environment-based:dev.example.com
staging.example.com
qa.example.com
uat.example.com
Service-based:api.example.com
auth.example.com
payments.example.com
internal.example.com
Region or tenant-based:us.example.com
eu.example.com
client1.example.com
Technical Advantages:
- Passive and low noise
- Predictable in nature
Technical Constraints:
- Time Consuming and requires pattern analysis
Subdomain enumeration is not a single command or a one-time activity. It is an iterative reconnaissance discipline that directly shapes the effectiveness of a security assessment.
In modern Red Team engagements, the difference between Surface level findings and high impact vulnerabilities often lies in how comprehensively the attack surface was mapped. A structured, multi-source enumeration strategy ensures that critical assets are discovered early and assessed thoroughly.
Leave a Reply