
In an ideal pentesting setup, installing tools is trivial cloning a GitHub repository, installing dependencies, resolving errors, and carry the activities. Security testers often, more increasingly now come across the below:
- Hardened endpoints with no admin privileges
- No internet access or outbound restrictions
- No package managers (pip, apt, brew)
- Restricted PowerShell or script execution
- Time-boxed engagements where setup overhead directly contributes to testing time
In such environments, static or portable binaries become more than a convenience—they become a requirement.
What Are Static / Portable Binaries?
For testers static binaries mean “Less setup, fewer failures, and more time spent actually testing”. A static (or portable) binary is a self-contained executable that includes:
- The application logic
- Required libraries
- Runtime dependencies (where possible)
This allows the tool to:
- Run without the original language runtime (Go, Python, etc.)
- Be copied directly to a target system
- Execute immediately without installation steps
Why Go-Based Tools Work Exceptionally Well as Static Binaries?
Most modern offensive security tooling has shifted toward Go, and for good reason. Main reason why its shifting towards go-based tools are:
- Compile into single-file executables
- Are resilient in hardened enterprise environments
- Support cross-compilation (Windows, Linux, macOS)
- Do not require Go to be installed on the target
- Handle dependencies predictably
Below mentioned are some of the most popular go-based tools that can be converted to static binaries:
- Nuclei
- Amass
- Subfinder
- Waybackurls
- Gau
- Godap
- Kiterunner
- S3scanner
- Gospider
- Hakrawler
- Katana
- Ffuf
- Httx
- Qsreplace
- Crlfuzz
- Dalfox
- Naabu
- Trufflehog
- Gitleaks
- Urlfinder
- unfurl
The binaries for all of the above-mentioned tools can be created using just few simple commands:
Step 1: Open Command Prompt and type the below mentioned commands:
set CGO_ENABLED=0
set GOOS=windows
set GOARCH=amd64Step 2: Clone the respective repositories of the all the tools and in command prompt use the below command:
go build -ldflags="-s -w" -o toolname.exeThe binaries for all the mentioned tools in this blog has been created and uploaded to the below mentioned GitHub Repository incase people don’t want to go through the hassle of creating it themselves:
GitHub Repo: https://github.com/KhukuriRimal/Static-Binaries/tree/main
Creating Static Binaries of Python Based Tools
Similar to Go, Python is another language used to automate and make lot of tools for VAPT, Red Teaming and Active Directory Pentesting. Its infact the most common, popular and used language. Popular tools like SQLMap, Ghauri, Dirsearch, Ldapenum, Bloodhound etc are all python based tools. However, unlike go-based tools, python based tools have some limitations on converting them to static binaries.
Python tools can be converted into standalone executables using PyInstaller, but this comes with limitations.
- Python binaries still bundle a Python interpreter
- Dynamic imports and runtime behavior can break
- Not all libraries freeze cleanly
- Platform-specific issues are common
That said, some Python tools do work reliably when packaged correctly. Not all python based tools can be packaged properly to create static binary, however to show examples, the below mentioned commands can be used to create static binary of some popular tools:
a. Sublist3r:
pyinstaller --onefile sublist3r.py --hidden-import=dns --hidden-import=requests --name sublist3r.exeb. Linkfinder:
pyinstaller --onefile linkfinder.py --hidden-import=jsbeautifier --hidden-import=bs4 --hidden-import=lxml --name linkfinder.exec. Secretfinder:
pyinstaller --onefile SecretFinder.py --hidden-import=jsbeautifier --hidden-import=requests --hidden-import=re --name secretfinder.exed. Ldapdomaindump:
pyinstaller --onefile ldapdomaindump.py --hidden-import=ldap3 --hidden-import=jinja2 --name ldapdomaindump.exeHow Static Binaries Save Significant Time in Engagements
In real assessments—especially internal VAPT, assumed breach, or red team operations—this difference is critical.
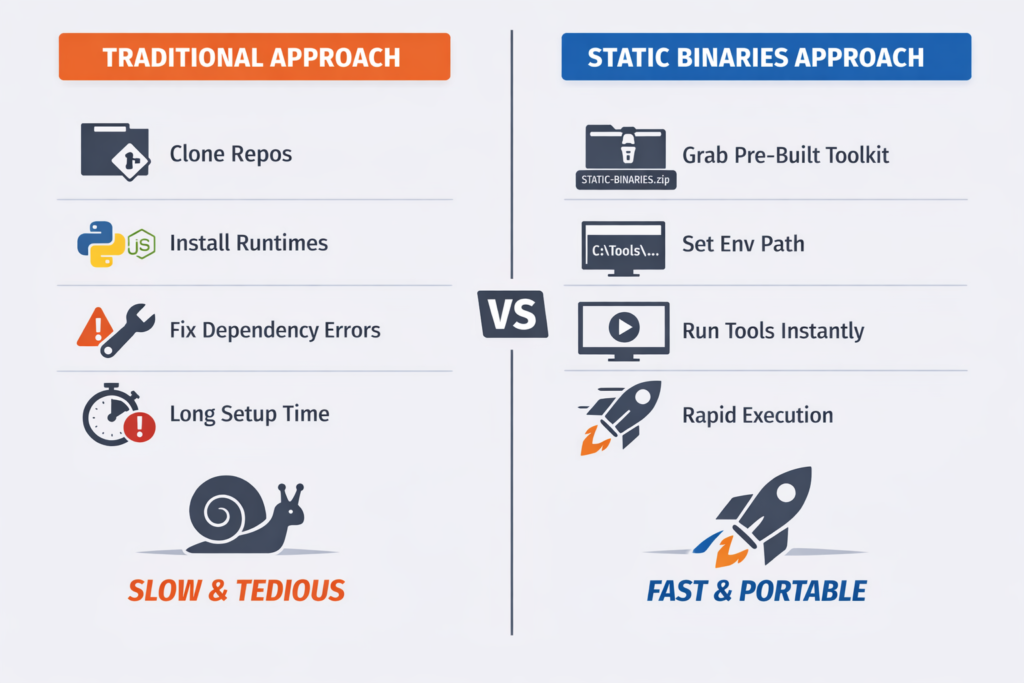
Using a Pre-Built Static Toolkit
Instead of building everything from scratch during an engagement, maintaining a pre-built repository of portable tools is far more practical.
For example, cloning a repository such as:
https://github.com/KhukuriRimal/Static-Binaries
This provides Precompiled static binaries, Consistent tool versions, Reduced setup errors and Faster deployment in restricted environments.
For pentesters, red teamers, and AD assessors working in real, hardened environments, maintaining a portable static toolkit is no longer optional, it’s a professional advantage.
Leave a Reply