
In modern security assessments, researchers and pentesters rarely start with direct exploits, they start with gathering information. One of the most underestimated reconnaissance tools is sitting in front of everyone which is the Google Search engine. When used strategically, Google Dorking becomes an attack surface mapper, unintentionally exposing sensitive assets, internal systems, misconfigurations, credentials, backups, logs etc. For red teamers and VAPT professionals, Google Dorking is not about random queries it’s about structured intelligence gathering.
What Is Google Dorking?
Google Dorking (also called Google Hacking) is the use of advanced search operators to precisely locate sensitive or misconfigured information indexed by search engines.
Why Google Dorking Is Extremely Powerful in Red Teaming and VAPT?
During offensive engagements, stealth and speed matter. Google Dorking helps you:
- Map digital footprint instantly
- Find low-hanging misconfigurations
- Discover forgotten assets
- Build attack chains faster
It’s passive reconnaissance with no alerts, no WAF triggers, no IDS noise. For red teams, this can often become the initial access enabler. Google Dorking becomes truly powerful when used to map people, infrastructure, credentials, third-party trust, and forgotten attack surfaces, not just exposed files. Below are high-impact scenarios attackers and red teams abuse in real engagements.
1. Social Media Enumeration (Employee & Target Profiling):
Google dorks helps in Identifying employees, roles, and organizational structure.
site:linkedin.com/in "company name" -jobs -hiring
site:linkedin.com/in "employee name" "company"
site:linkedin.com/in ("security engineer" OR "devops" OR "IT administrator") "company name"
site:linkedin.com/in ("CTO" OR "CISO" OR "manager") "company name"
site:github.com "company name"
site:facebook.com "company name" "employee"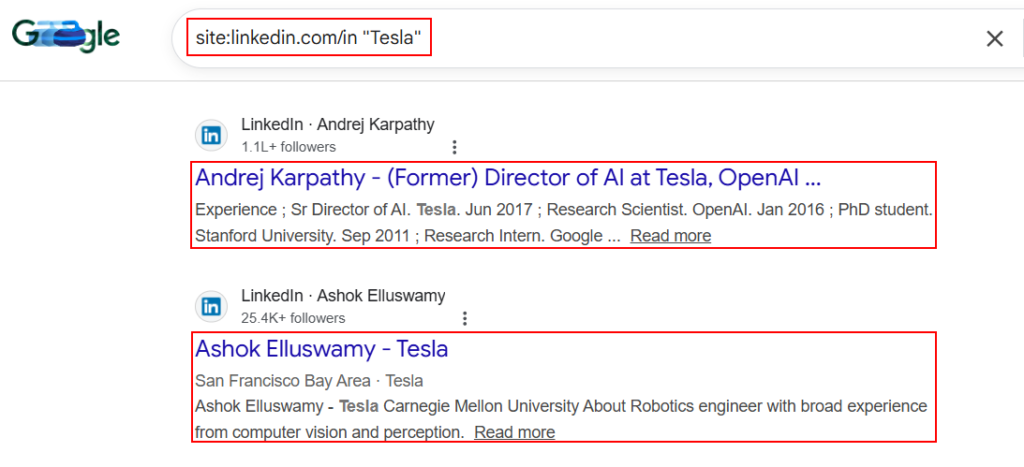
2. Email Address Harvesting:
Google dorks can be used in collecting valid corporate email accounts for password spraying, phishing campaigns, and MFA abuse during red team exercises.
site:example.com "@example.com"
site:pastebin.com "@example.com"
site:github.com "@example.com"
site:example.com ("@example.com" OR "mailto:")
site:example.com intext:"@example.com"
site:example.com (filetype:pdf OR filetype:doc OR filetype:docx OR filetype:xls OR filetype:xlsx) "@example.com"
site:linkedin.com "@example.com"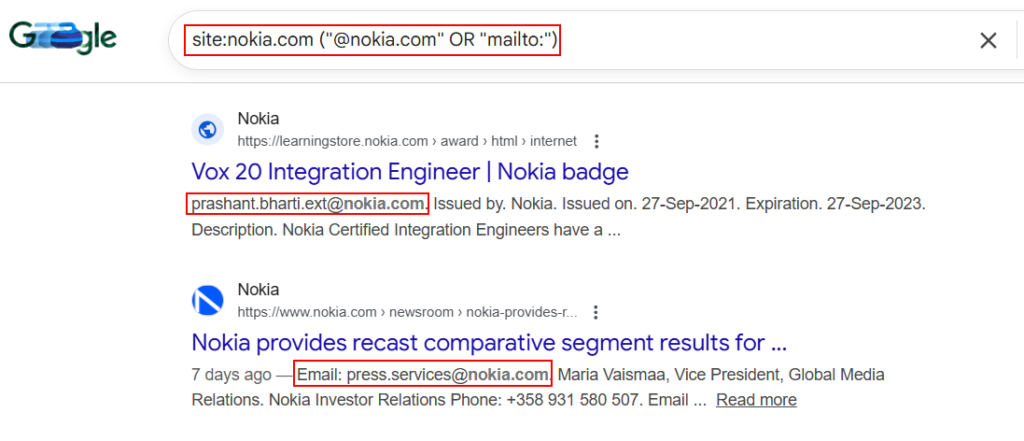
3. VPN Configuration Files Exposure:
Google dorking can be used to reveal VPN endpoints, encryption settings, and sometimes credentials enabling direct internal network access.
site:example.com filetype:ovpn
site:example.com filetype:pcf
site:example.com filetype:key
site:example.com filetype:crt
site:example.com filetype:wg
site:example.com filetype:json "vpn"
site:example.com filetype:pem
site:example.com filetype:pfx
site:example.com (ext:zip OR ext:tar OR ext:gz) "vpn"
site:example.com "group-policy" "vpn"
site:example.com "forticlient.conf"
intitle:"index of" "ovpn"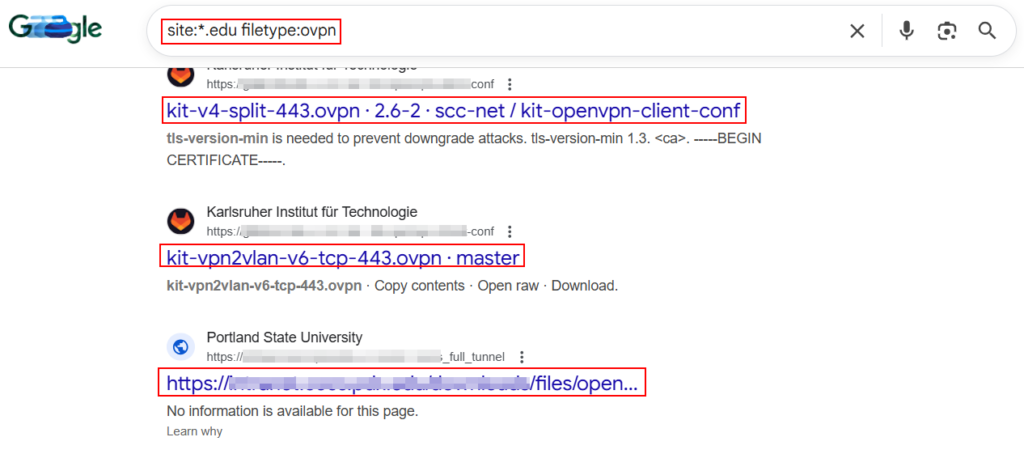
4. GitHub & Source Code Leaks:
Google dorking can help in uncovering hardcoded secrets, internal APIs, and infrastructure logic from public code repositories.
site:github.com "example.com" "password"
site:github.com "example.com" "api_key"
site:github.com "example.com" ".env"
site:github.com "example.com" "access_token"
site:github.com "example.com" "auth_token"
site:github.com "example.com" "secret"
site:github.com "example.com" "credentials"
site:github.com "example.com" "AWS_ACCESS_KEY_ID"
site:github.com "example.com" "s3.amazonaws.com"
site:github.com "example.com" "slack_token"
site:github.com "example.com" "settings.py"
site:github.com "example.com" "BEGIN RSA PRIVATE KEY"
site:github.com "example.com" "id_rsa"
site:github.com "example.com" (jdbc: OR mongodb:// OR MySQL:// OR posgres://)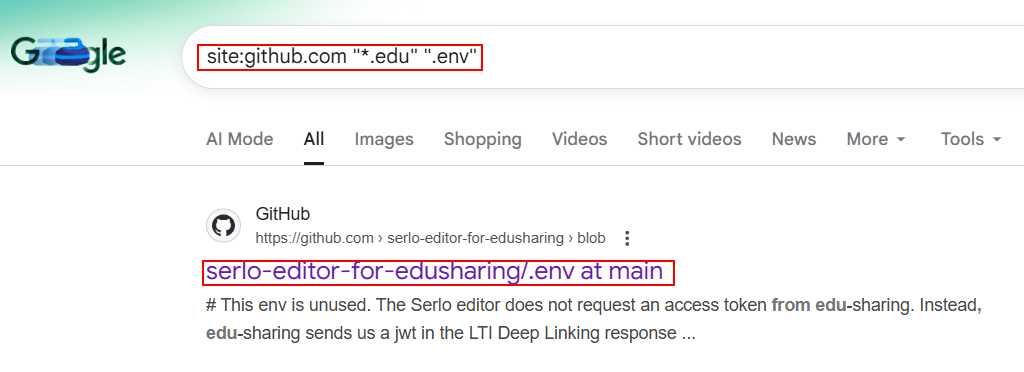
5. Cloud Storage & Backup Leaks:
Dorking can also be used in finding publicly accessible cloud buckets containing sensitive data, backups, and production assets.
site:s3.amazonaws.com "company"
site:blob.core.windows.net "company"
site:storage.googleapis.com "company"
site:blob.core.windows.net "confidential" "company"
("s3.amazonaws.com" OR "blob.core.windows.net" OR "storage.googleapis.com") "company"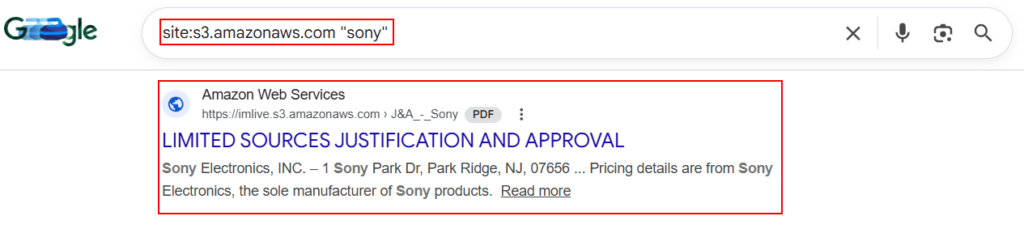
6. Backup Files Enumeration:
It can be used to Discover compressed site backups often containing full source code and credentials.
site:example.com filetype:zip
site:example.com filetype:tar
site:example.com filetype:gz
site:example.com filetype:bak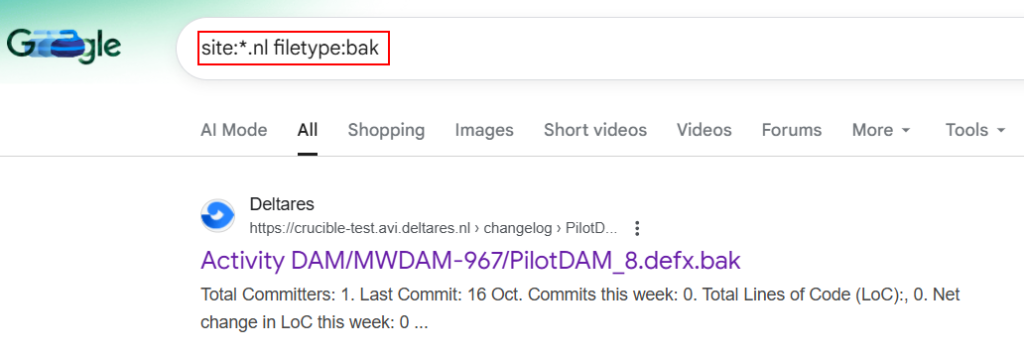
7. Database Dump Enumeration:
Google dorking also helps in locating leaked SQL files possibly revealing user data, password hashes, and application structure.
site:example.com filetype:sql
site:example.com "INSERT INTO users"
site:example.com filetype:dump
site:example.com filetype:sqlite
site:example.com filetype:backup
site:example.com (ext:zip OR ext:tar OR ext:gz OR ext:7z) "sql"
site:example.com "username" "password"
site:example.com "users table"
site:example.com "migrations"
site:example.com (ext:zip OR ext:gz) "users.sql"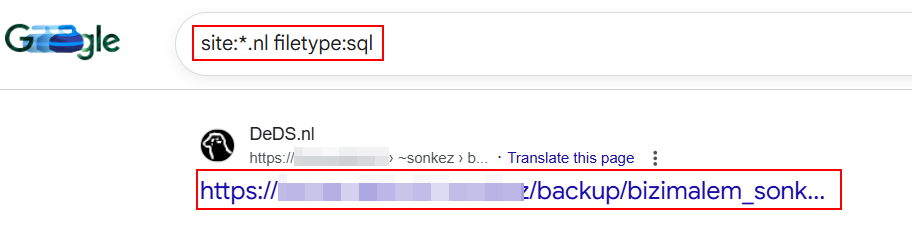
8. Log Files with Sensitive Data:
Google dorking can also be used to extract sensitive tokens, internal IPs, error messages, and debugging information from exposed logs.
site:example.com filetype:log
site:example.com "exception"
site:example.com "stack trace"
site:example.com filetype:trace
site:example.com filetype:debug
site:example.com "NullPointerException"
site:example.com "SQL syntax error"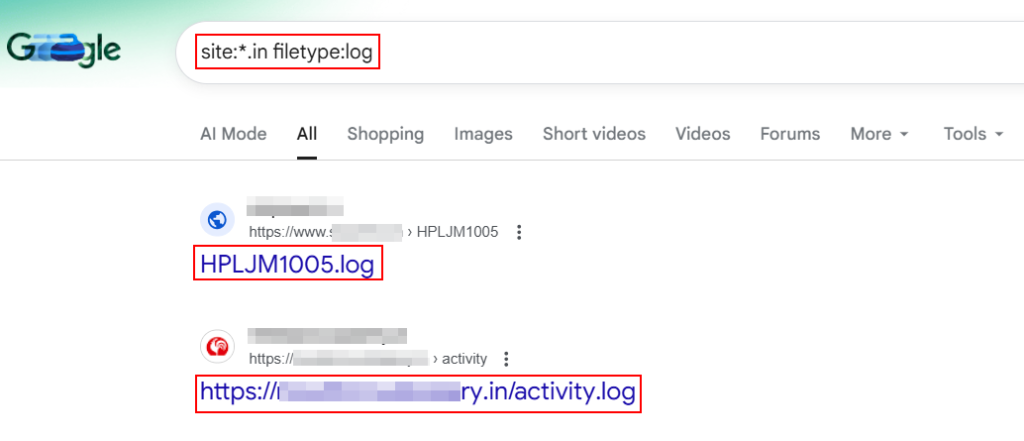
9. Admin Panel Enumeration:
Google dorking also helps in Identifying admin panel or management interfaces that frequently lack proper authentication and monitoring.
site:example.com inurl:admin
site:example.com inurl:portal
site:example.com inurl:dashboard
site:example.com inurl:internal
site:example.com inurl:administrator
site:example.com inurl:controlpanel
site:example.com inurl:manage
site:example.com inurl:console
site:example.com inurl:jenkins
site:example.com inurl:gitlab
site:example.com inurl:sonarqube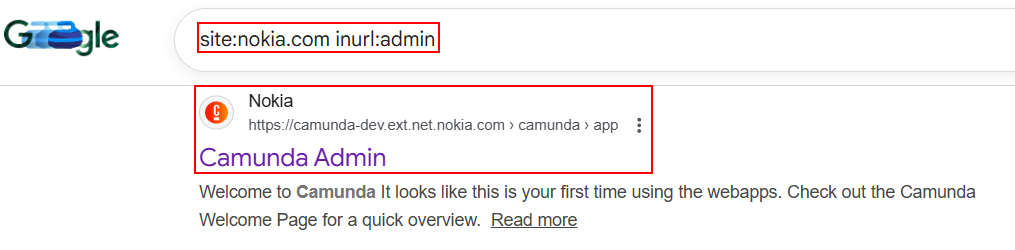
10. Staging / Dev Environments:
In red team exercises identifying staging and development environments can often be goldmine as they tend to be less secure than production instances. Google dorking can also be used in finding poorly secured pre-production systems commonly used to pivot into live environments.
site:example.com inurl:dev
site:example.com inurl:test
site:example.com inurl:staging
site:example.com "debug=true"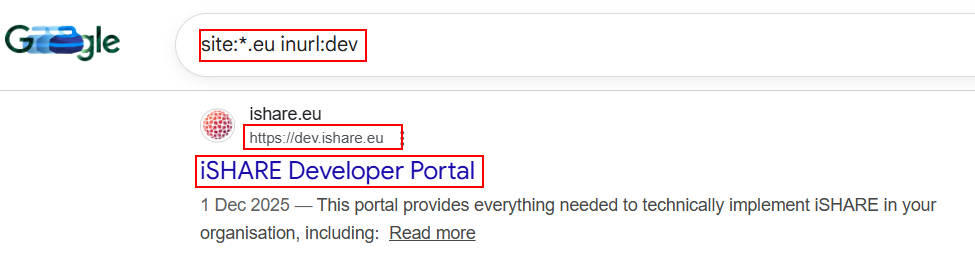
11. Exposed Environment Files:
Dorking can also be used to search for environment files containing secrets such as database credentials, API keys, and cloud access tokens.
site:example.com filetype:env
site:example.com ".env"
site:example.com ".env.bak"
site:example.com ".env.old"
site:example.com ".env.local"
intitle:"index of" ".env"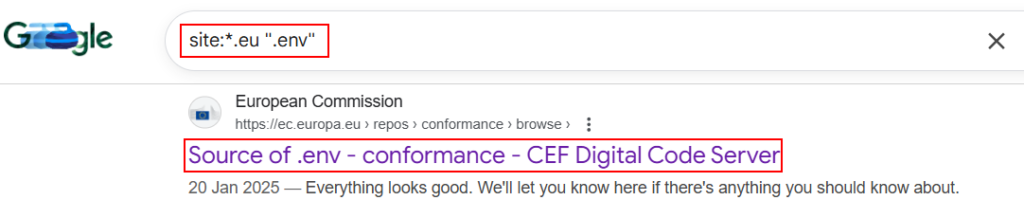
12. Password Files & Credential Lists:
Google dorking can help Locate plaintext username-password combinations accidentally published online.
site:example.com filetype:txt "password"
site:example.com filetype:csv "username,password"
site:example.com (ext:zip OR ext:tar OR ext:gz) "password"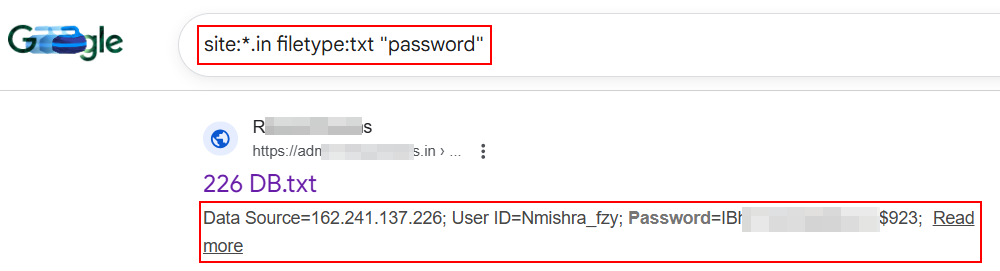
13. Firewall / Network Device Configuration Files:
Google dorking can also assist in revealing internal network architecture, VPN setups, and security device settings of oraganizations.
site:example.com filetype:conf "vpn"
site:example.com filetype:cfg
site:example.com "asa configuration"
site:example.com filetype:ini
site:example.com filetype:backup
site:example.com "asa configuration"
site:example.com "show running-config"
site:example.com "config firewall policy"
site:example.com "set deviceconfig"
site:example.com (filetype:cfg OR filetype:conf) "password"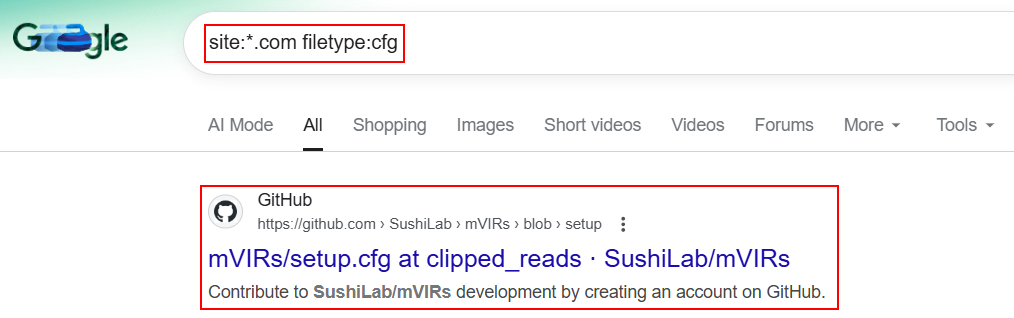
14. API Endpoints & Swagger Documentation:
API Collections and documentation pages can be identified using Google dorking which will provide a full blueprint of backend services and exploitable API endpoints.
site:example.com inurl:swagger
site:example.com inurl:api-docs
site:example.com inurl:openapi
site:example.com inurl:swagger-ui
site:example.com inurl:swagger-ui.html
site:example.com inurl:/swagger/index.html
site:example.com inurl:openapi.yaml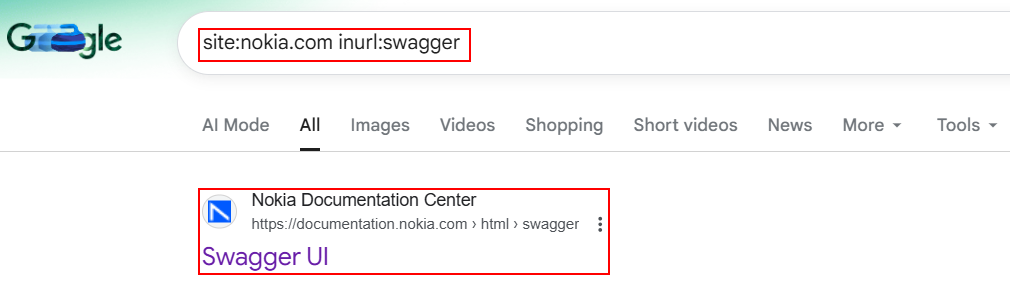
15. IP Addresses Enumeration:
IP Address public or private can be enumerated using Google Dorking.
site:example.com "10."
site:example.com "192.168."
site:example.com "172.16."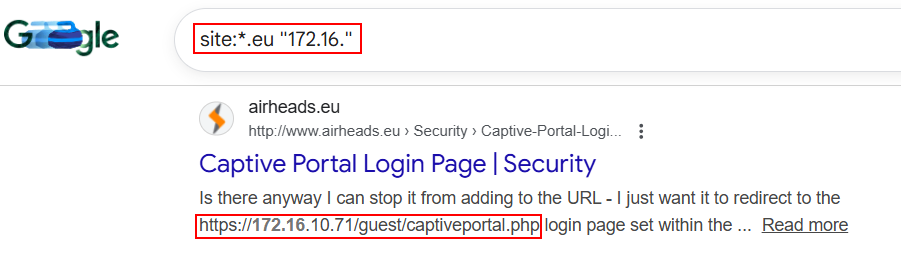
16. Webcams & IoT Devices:
Google dorking can also be used to discover exposed live feeds and unsecured smart devices on the internet.
inurl:view/view.shtml
inurl:viewerframe?mode=
intitle:"Live View"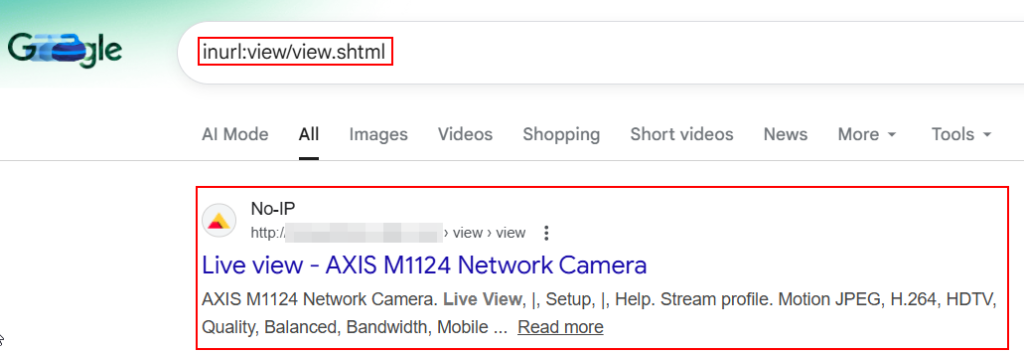
17. PDF & Document Intelligence:
Google Dorking can also help in Extracting operational intelligence, software details, and internal communications from PDFs and docs.
site:example.com filetype:pdf
site:example.com filetype:docx
site:example.com filetype:pdf "strictly confidential"
site:example.com filetype:pdf "confidential"
site:example.com filetype:pdf "internal use only"
site:example.com filetype:pdf "restricted"
site:example.com filetype:pdf "private and confidential"
site:example.com filetype:pdf "vpn access"
site:example.com filetype:pdf ("confidential" OR "internal" OR "restricted")
site:example.com filetype:docx ("confidential" OR "internal" OR "restricted")
site:example.com filetype:doc ("confidential" OR "internal" OR "restricted")
site:example.com filetype:ppt ("confidential" OR "internal" OR "restricted")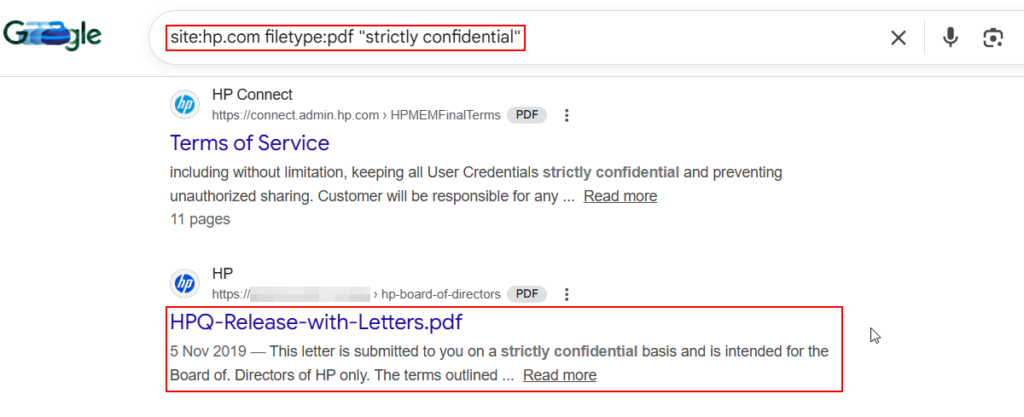
18. Error Messages & Stack Traces:
Error messages and Stack traces generally reveals backend technologies, file paths, and logic helpful for targeted exploitation, Google Dorking can be used to identify such instances as well.
site:example.com "Fatal error"
site:example.com "Warning: include"
site:example.com "Traceback"19. Subdomain Enumeration:
Google Dorking can also be used to identify or enumerating subdomains.
site:*.example.com
site:dev.example.com
site:old.example.com
site:beta.example.com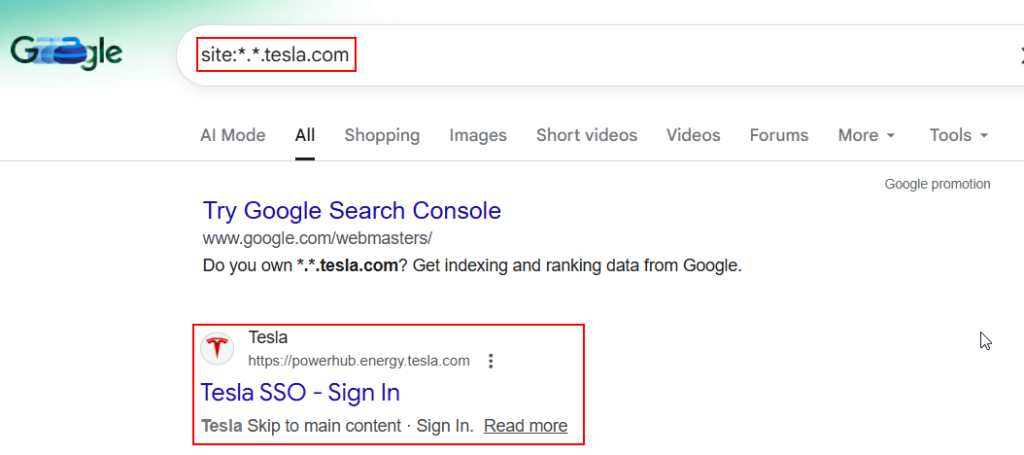
20. Public Trello / Jira / Confluence Data
Google Dorking if done properly can also assist in finding exposed Trello, Jira, or Confluence pages containing credentials and internal plans.
site:trello.com "example.com"
site:atlassian.net "example.com"
site:confluence "example.com"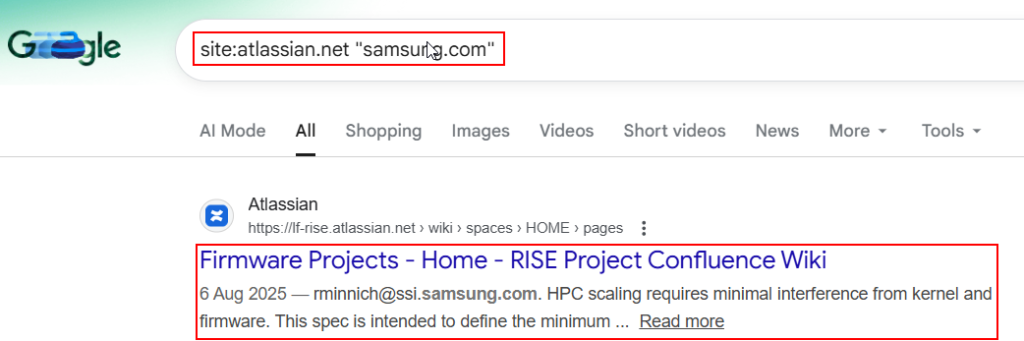
21. Exposed SSH Keys:
Leaked or exposed SSH Keys can be identified using Google Dorking.
site:example.com filetype:key "BEGIN RSA PRIVATE KEY"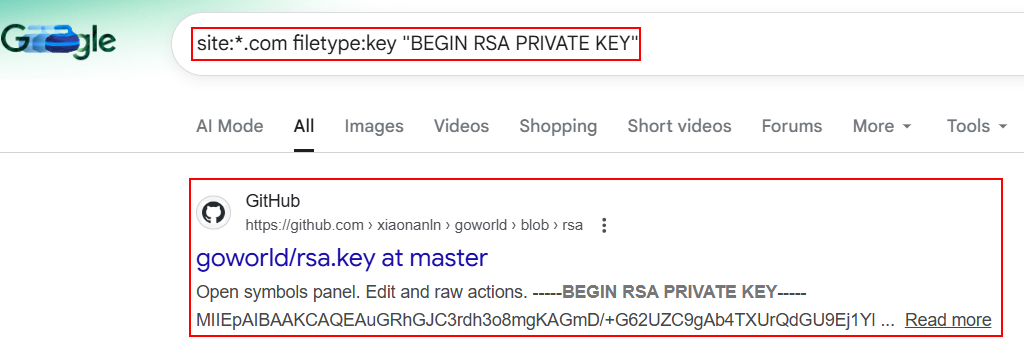
22. NNTP / Google Groups Intelligence:
It can help in Surfacing historical discussions, leaks, and infrastructure references tied to the target.
site:groups.google.com/forum "example.com"23. Paste Sites (Credential Dumps):
Google Dorking can be used in Identifying leaked data from breaches shared across paste platforms.
site:pastebin.com "example.com"
site:ghostbin.com "example.com"
site:paste.ee "example.com"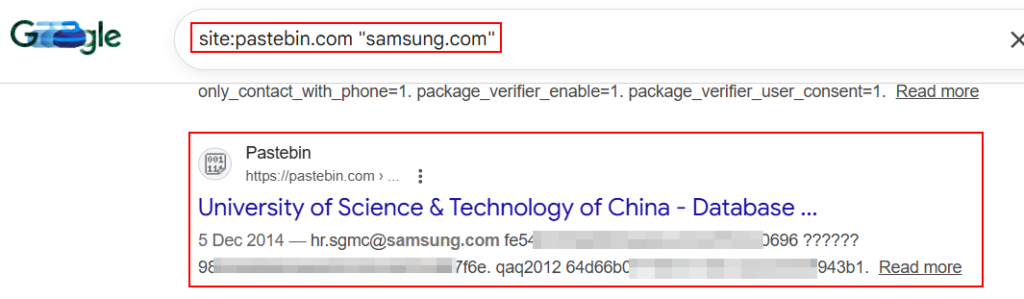
24. Configuration & YAML Files:
Google Dorking can be used to identify exposed application secrets, API tokens, and infrastructure settings.
site:example.com filetype:yml
site:example.com filetype:yaml
site:example.com filetype:json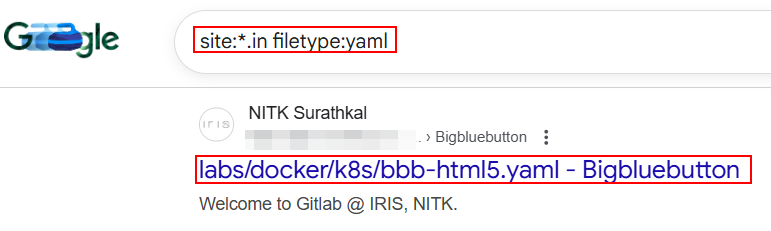
25. Exposed Monitoring & Dashboards:
Dorking can also help in finding unsecured Grafana, Kibana, or Prometheus instances exposing real-time system data.
site:example.com inurl:grafana
site:example.com inurl:kibana
site:example.com inurl:prometheusTo make life easier, a Google Dorking page has also been created in the website, you can visit the below mentioned link or click the “Google Dorking” menu.
https://cybersecwriteups.com/category/google-dorking
In red teaming and VAPT, Google isn’t just a search engine, it’s a passive reconnaissance framework that continuously indexes human mistakes, misconfigurations, and forgotten assets waiting to be looked into.
Leave a Reply